
The Twitter blue checkmark started as a security control and slowly turned into social status. What happened to the security part?
Trying to come up to speed on cloud security at AWS re:Invent 2022? Here’s my session guide for attendees of all levels.

CJ Moses, CISO of AWS, delivers a leadership session to highlight the state of security and what’s next.

Leading up to AWS re:Invent, these 5 great new features launched to help your cloud security practice.

Mastodon is an open-source federated social media network. Twitter users are flocking to it only to find furstration.

Toasters work so well that you forget they need maintenance. If we could get to taht level with cybersecurity controls we’d be lucky…until we weren’t

Your centralized security needs to support a variety of teams building in the cloud…and they all have differing levels of maturity.

For stronger security, stop focusing on cybercriminals and pay attention to how your teams are building in the cloud.

AWS re:Inforce brought the people side of security into sharp focus.

Lacework gets named to the Forbes Cloud 100 list for 2022.

Compliance is a snoozer of a topic. It shouldn’t be.

The keynote at AWS re:Inforce will send a strong message about security. Here’s what I want to hear from AWS.

AWS uses a very specific session structure for their events. Here is the key to understand the differences.

Visibility is often cited as the top requirement for any cloud security practice…but what is it exactly?

Too often security is a singular focus or area of responsibility. It doesn’t work like that. Security is part of a bigger whole.

The RSA Conference is jam packed with great content. Here’s how you can get the most from your week in San Francisco.

The Shared Responsibility Model provides the roadmap for cloud success. Here’s how to use the model to your advantage.

Machine Learning is a valuable and useful tool…when used correctly. Hear from one of the best how to do just that.

Okta is responding to a public cybersecurity incident, what can we learn from how they handled communications?

With cybercriminals becoming bolder, it’s not surprising that we’re seeing more big name breaches.

CloudFlare launches a new API Gateway product, will is shake up the market?

Kubernetes is challenging to configure and maintain on the best of days. Here’s where to focus your security efforts.

Attackers can find your cloud misconfigurations with almost no effort, why can’t you?

Once you’ve aggregated all of your AWS Security Hub Findings, here’s one way to visualize and analyze them.

Once you’ve aggregated all of your AWS Security Hub Findings, here’s one way to visualize and analyze them.

Are NFTs, Web3, and Blockchains useful? Or just hype?

Two minutes of work can stop hackers in cold in their tracks.

Bug bounties help bridge the gap between security researchers and companies.

The risks of smart contract bugs are quickly becoming apparently. They can cost millions.

Misconfigurations in Amazon S3 keep happening. Here’s why and how to stop them.

The NFT/Web3 world certain is the wild west…and some projects are way, way more wild.

If you can’t read the code in a Web3 contract, do you really know what it’s going to do?

If a smart contract works as coded and the code is wrong, is the contract valid?

Anytime there’s a security issue, someone gets labelled a hacker. Is that the right term?

Data Privacy Day is upon us once again, here’s an interesting discussion around key privacy topics and how they might impact you.

AWS Security Hub Findings are great, but they can be better. Here’s a simple pattern from the AWS team to enrich those findings automatically.

“Um” is not a great call to action, but sometimes it’s all you’ve got.

Can you—as a user—understand an app or service’s security posture? If so, how?

DevOps and DevSecOps are terms that are thrown around a lot. What do they really mean?

Should be able to encrypt your communications? The debate is on…again

A lot of risk decisions are made in the dark…why?

Everything in the cloud works on a shared responsibility model. Here’s how it works.

It’s exciting building solutions with the latest frameworks and technology. Is that the best route to meet our goals? What ARE our goals?

When we talk about privacy, what are we really talking about? The formal definition of privacy is definitely outdated. What would a good definition be?

If the goal of cybersecurity is to make sure that the system you are building works as intended and only as intended, what about stopping hackers?

Security and privacy are inextricably linked. Why aren’t they at the core of all technology?

Log4j is hiding in a number of your systems. Here’s help to plan out your response.

No one can predict the future. Here’s what the data shows will be trending in cloud security in 2022.

Every year AWS sets the tone for all of cloud at AWS re:Invent. Here’s what you can expect in cloud computing for 2022.
The leadership session at AWS re:Invent provide a deeper dive into a specific area of focus. Stephen Schmidt, CISO at AWS takes the stage to talk all things security.

Amazon Inspector first launched in 2015. Now in 2021, it’s re-launching with a brand new architecture and a host of new features.

Amazon Inspector first launched in 2015. Now in 2021, it’s re-launching with a brand new architecture and a host of new features.

AWS re-launches a dramatically improved Amazon Inspector, a software vulnerability discovery/management service.

Most security practices make the same set of mistakes when moving to the cloud. This talk looks at those mistakes and how to avoid them.

There are massive opportunities to advance your security practice as your business moves into the cloud. This talk provides a step-by-step approach that will help you maximize them.

DevSecOps is the latest in a long line of buzzwords. The core makes sense: work on security earlier. But why isn’t this everywhere? Here’s the biggest mistakes teams are making trying to “do” DevSecOps.

Passwords suck. Why are we forced to follow these weird rules. Do they really keep us safe? Here is a solid way to safely handle all of your passwords.

Twitch has been hit by a major data breach. 165GB of critical information was leaked on 4chan. What will the impact be? Will this cause even more streamers to leave?

There are a lot of acronyms related to cloud security. What do they mean and can they help you?

AWS re:Inforce returns in person and provides a deeper look into how AWS views security.

The Microsoft Edge browser team is conducting an experiment in an attempt to increase the cybersecurity of the browser and how it handles javascript. At stake? One of the major performance features.

A new report from a United States Senate Committee gave 24 US department and agencies an average grade of C- in cybersecurity. That’s not good.

The region of Lazio was hit by a ransomware attack and is struggling to recover from this attack on critical infrastructure. BlackMatter, a new ransomware supergroup, just announced they wouldn’t conduct these types of attacks. What does it mean for the future of ransomware?

EA got hacked and 780 GB of source code was stolen. The hackers attempted to extort EA and when they didn’t pay, the data was dumped online.

The US government takes steps to codify cybersecurity requirements for critical infrastructre.

Twitter’s latest transparency report shows a low uptake for the multi-factor authentication feature. This is a great security control that’s easy to use. What’s going on?

The Pegasus Project is a collaborative effort by a number of media and advocacy organizations around to the world. With their work, they are shining a light on nation state use a specific malware tool: Pegasus spyware.

There are now 5 seniors leaders in the US federal governments with cybersecurity as their primary mandate. Is this going to be a problem?
Two new resources launched to help people understand the challenges associated with ransomware; StopRansomware.gov and RansomWhe.re

Are security agent programs bad? Don’t even answer, that’s a ridiculous question.

REvil has been one of the top ransomware groups for the past few months but they’re suddenly offline. No note, no warning, just gone.

Long after the headlines pass, victims of ransomware are left struggling to get back to “normal” operations. It’s a long, challenging road back.

The out-of-band patch for PrinterNightmare on Microsoft Windows doesn’t completely fix the issue. What are IT and security teams to do?
The REvil gang attack Kaseya, an IT management platform, and that got them access to 800—1,500 more businesses without any additional effort setting the new normal.

Ransomware is absolutely everywhere. What is going on? Why is ransomware so effective? Is there anything we can do about it?

Criminals are using real apps they’ve made and a push to remove ads to harvest Facebook credentials in order to gain more personal information to sell.

PrinterNightmare is a high severity vulnerability that affects all versions of Windows and is being actively exploited…on a long weekend 😬
Microsoft Windows 11 will require a Trusted Platform Module (TPM) on all PCs. Will this long-needed requirement help or hinder?

Some WD My Book Live users had a shock this week as hackers remotely wiped their data. What can they do about it?

Apple is under fire on a number of fronts. The biggest issue this week is several bills introduced in the US. A key issue? The ability to “sideload” apps on your iPhone.

A discussion about the evolution of security in the cloud. Security is now becoming a critical piece of a developer’s pipeline, what does that actually mean?
Celebrating three years of the CISO/Security Vendore Relationship Podcast

A purely digital RSAC 2021 kicks off looking back at a challenging year and to the challenges ahead for the security community.
In software, developers often don’t have a choice. Speed becomes a business imperative for survival and to stay competitive.
An all virtual RSAC 2021 kicked off today. What are the themes? What do we expected to see? This discussion on theCube has you covered.
AWS IAM has been going strong for 10 years! To celebrate the anniversay, this four part series by various AWS Heroes, highlights some key features of the service

I recently made a career move and it’s allowed me to re-double my efforts in the community. What do you want to learn about cloud and security?
iOS 14.5 introduces App Tracking Transparency or ATT. Here’s what it means to you.
No other technology revolution has induced more fear, uncertainty, and doubt for so long than the cloud. This post explores the “why” of it and more…

Ubiquiti suffered a data breach and makes it worse by not communication clearly with it’s customer base.

iOS 14.4.2 fixes a critical cybersecurity issue. Make sure to update now.
Setting a new cloud account well is reasonably simple, but what about accounts that are already active? Here are some tips to add guardrails after the fact.

iOS 14.4.1 fixes a couple of critical cybersecurity issues. Make sure to update now.

Security and privacy are linked yet for some reason, you see privacy experts ignoring the impact of security and security experts who are unconcerned with privacy. Why?

As you continually evolve your use of AWS products and services, it’s important to consider ways to improve your security posture and take advantage of new security services and features. This session shares architectural patterns for meeting common challenges, service quotas, and tips and tricks for continually evaluating your architecture against …

Passwords are the worst. Trying to pick a “secure” one makes the whole thing worse. Every site and service has it’s own variation on the “rules” for making a strong password and it’s hard to remember what you’ve set your password to.
Are those rules really making our passwords stronger? Do we need so many …
Apple recently launched macOS Big Sur and a security researcher’s post vent viral highlighting a steady stream of communications that “phone home” detailing what apps you’re using on your system. What’s going on here?
Is privacy promoting Apple actually spying on every app running on every macOS system around the …
Ad-tech, digital marketing, and the surveillance economy are worth billions and billions of dollars. It all hinges on the ability to target ads and you can’t target ads without tracking users and their devices.
A privacy-focused design decision by Apple for iOS 14 puts Facebook on edge and Google on notice. What is the IDFA? What happens in …

Epic Games is current waging war on Apple and Google over the right to distribute apps to mobile users. There’s been a ton of excellent coverage of the issues, but it’s usually missing one key perspective; what do we as users get from the App Stores?

The Canada Revenue Agency suffered a large breach exposing over 5,000 citizens to COVID-19 benefit fraud. This issue exposes some of the challenges of providing authentication services to millions of citizens. Why did this happen? And what can we do to protect ourselves?

On July 15th, 2020, Twitter was hit with the most visible hack of a social network of all time. 130 of the top accounts tweeted out a bitcoin scam. A month after, have we learned anything? What’s the impact of continuing to use Twitter?

To make sure that systems work as intended and only as intended. That’s the goal of cybersecurity.

The President has promised to ban TikTok in the United States for national security reasons. Is that the case? Are there real security & privacy concerns or is this purely a political move?

Is a social network focused on dancing, lip syncing, and fun a threat to national security just because of who owns it? Is TikTok a threat to national security? Do you need to worry about it you or your family using it?

Video conferencing platform Zoom has been in the news almost constantly over the past few weeks. At first it was hailed as a tool to help reduce this isolated feeling all of us are experiencing, then it was a pile on for security and privacy issues, and finally the last two weeks have started a redemption story.

Security is often spoken of in absolutes. Is this secure? Is that insecure? The reality is that security is a spectrum. It is a series of implicit and explicit decisions made to meet the business needs within an acceptable risk tolerance.
What is an acceptable risk? How can you determine what threats pose a risk to your work? How likely are those …

Technology is omnipresent in our lives. From the time you wake up and check the weather to the time your head hits the pillow, you will have spent at least a quarter of your day interacting with technology. In this talk, Mark Nunnikhoven, vice president of Cloud Research of Trend Micro, will navigate you through your average 24 hours and uncover …

CBC’s Go Public pointed out the rising rates of e-transfer fraud and consumers are shocking. The expectation was that e-transfers were safe and convenient…turns out, not so much.

Letting customers know about a security vulnerability is never an easy thing. From the logistics of it to the reputation management issues. But this is a critical aspect of delivery software and services. What’s the best way to tackle this problem?

Zoom.us had a pretty egregious security issue this week. Their response was poor despite the best efforts for responsible disclosure by the security research who discovered the issue. While this issue has dominated tech headlines, the real issue is much more significant and commonplace.

Cybercriminals don’t always use complicated technical attacks to get around your cybersecurity. Sometimes—probably more often than we care to admit—it’s the really simple stuff that works and what’s simpler than an email?

Huawei was recently put on the US Entity List from the US Department of Commerce. That essentially means that it needs a license to receive technology from US companies…a license that is a default “no” and in this political climate, a definite “no”.
Politics aside, what does that mean for Huawei smartphone users?

The NBA playoffs are in full swing and there’s a huge rules controversy around one superstar’s—James Harden—jump shot. Is it a foul? Regardless of the answer, it pushes the rules to the limit. The same thing happens in cybersecurity. People just trying to get their job done will push the rules to the breaking point…and sometimes …

A recent report from the Canadian Commission for Complaints for Telecom-television Services (CCTS) saw a dramatic increase in complaints with billing being one of the top reasons. That’s not especially noteworthy in an industry known for poor customer service…until you dig a little deeper.

A recent study by NCSU found that there are way more API keys and tokens uploaded to GitHub than previously thought. In fact, there’s almost a near constant stream of secrets being exposed…why?!?

Google recently announced a new, all-in-the-cloud gaming service called Stadia. For gaming fans, there’s a lot of potential that—fingers crossed—hopefully pans out.
But the design of the system is an implementation of a pattern we use in securing high sensitivity data as well.
Has this pattern’s time finally arrived?

A recent survey from RightScale showed a lot of confusion around cloud computing costs. The common take away? Organizations are surprised at how high their cloud bills are. Similarly, the community was surprised at the size of Lyft’s commitment to AWS (around 8 million per month).
But the root of this problem isn’t what you think.

I you were just starting to try and understand the cybersecurity problem space, a CEO or CIO working to better grasp the challenges facing your organization, how would the industry look? Would you be able to spend wisely? To make decisions taht would actually improve the security of your organization? My view from RSA 2019 in San Francisco

We rely on some digital services for critical functions around security and privacy. Trusting those services is paramount to their success and ours. But it can be difficult to trust when you don’t know what’s going on behind the scenes. Gag orders from the courts can amplify those trust issues. The idea of a warrant canary can help to …

There has been a significant increase in DNS hijacking attacks over the past couple of months…and why not? It’s a simple, direct way for cybercriminals to take over an organizations identity or to intercept critical communications.

Cybersecurity is a major topic when it comes to modern elections. With Canada probably going to the polls in the fall, discussion is heating up about the potential impact of cybersecurity this election cycle. The good news? Canada’s election infrastructure is well protected. The challenge will be with various political parties and their …

Security research can be a tricky thing. Depending on where you are and what jurisdiction you fall under, the research you conduct may be illegal. That can give companies who are resistant to outside researchers the ammo they need to strong arm research teams. What’s the best way forward?

GDPR has been in effect for a few months and we’re starting to see the first major rulings. Google was just hit with a 50m Euro fine for not being clear enough in their intentions with user data. Is this a turning point? While regulation and legislation is typically followed to the letter, there are a lot of areas of GDPR that have specific …

Network security is struggling to keep up with the reality of how organizations are build and connect today. From hybrid network (on-premises and in the cloud) to large mobile user bases, traditional network security—push everything through a choke point—is well past it’s best before date. What’s next?

Security metrics are hard. But that doesn’t mean you should ignore them. In fact, a lot of teams are measuring the WRONG things which leads them down a path where efforts are being spent in areas that aren’t driving to their bigger goals.

Cyberattack attribution is HARD. But time and time again, we’re seeing attributions—who carried out the attack—made publicly with little to no evidence presented. Worse, these attributions are having real world impacts…

Trust is a tricky thing. Dotto Tech posed a number of great questions about trust in business and online that got me thinking. Do you trust the technology you’re using? How far? With what data? So many questions, here a few more to help you find some answers…
During a large incident response, bringing everyone together to a “war room” can be the difference in a speedy recovery, but there are downsides as well. The biggest? Fatigue & burnout. How do you monitor and handle that?

Google recently conducted a complete security & privacy review of various APIs associated with Google+. The result? The service is shutting down and they found a vulnerability. Did they take the proper steps in disclosing the issue?

With the Bloomberg report on hardware hacking looking more in doubt, more and more politics are coming into play. Anytime you evaluate news, it’s important to look at things objectively. Here are a few tips around evaluating cybersecurity news.

Bloomberg has an absolutely earth shattering report citing a hardware supply chain attack that—they say—impacted several big names. Here’s why this type of attack is so difficult to defend against but also near impossible to execute.

Criminals are winning the battle against security practitioners. Need proof? Look no further than the new headlines in any given week.
Billions of dollars are being spent on the latest and “greatest” tools, and millions of people hours are being exhausted in the defence of our data. Yet with all this effort, it remains trivially easy for most …

October is National Cybersecurity Awareness Month (#NCSAM). Look for tons of great content online as the community comes together—globally, not just nationally—to try and raise awareness of cybersecurity and privacy issues.

Security is a quality issue. Except we don’t treat it that way and that’s costing us dearly.

With the initial set of cybersecurity basics segments done, I’m think it’s worth moving to a “basics” basics series. The goal would be to help everyone understand how the internet works, how email is structure, etc. Thoughts?

Built-in security is always best. That’s “security by design” but when that fails (due to mistakes, oversight, humans), built-in security steps up…or, um, in.

In your personal life you’re assessing risk constantly whether you know it or not. In the digital world the same thing happens BUT you probably don’t have the required context to make an informed decision.

Risk assessments are useful when kept in context and continually updated. A penetration test (or pen test) is when your system undergoes a “friendly” attack with the idea of find issues before cybercriminals do. Together they are a strong set of practices to help you defences.

Personally identifiable information (PII) and Personal Health Information (PHI) are critical concepts. They help identify information that needs additional safeguards and care.

Who did it? It’s a powerful question and the answer to “What is attack attribution?”

Authentication and authorization are two critical concepts that are intertwined. Understanding the difference and their purpose is key to understanding cybersecurity.

Hackers and cybercriminals are all “malicious actors”. While you may not know who is attacking a system, having a better understanding of common motivations is important.

Malicious software (malware) is an umbrella term that covers a number of different types of software designed to do bad things…but those specific categories don’t mean to much day-to-day when it comes to defence…

Perspective is a tricky thing….maybe the hardest aspect of cybersecurity

What is a password? Why do we use them? Why are they so frustrating? …some answers

Continuing the “basics” series, here’s an easy way to understand the terms: vulnerability, exploit, threat, and risk

The basics starts with understanding the goal of security. It sounds simple but the goal is to make sure whatever you build works as you intend…and only as you intend!

A friend highlighted a real issue: there isn’t enough material about basic cybersecurity that’s easily relatable.

Connecting with others is critical but it can also pose a risk. It’s important not to “leak” information needlessly. This is a practice know as operational security. It’s critically important…and often ignored.

Security is there to ensure that the systems you build work only as intended. Part of that is realizing the potential for abuse and ensuring that the system and users can continue to work safely…there’s a LOT of work to do.

Getting your first cybersecurity role can be difficult. Is part of the problem how organizations are hiring talent?

Passwords are a horrible way to verifying identities but they are the best thing we currently have that works at scale. Adding a 2nd factor to that verification significantly increases the security of the system. But how can you add that factor without sacrificing usability?

You cannot stand at “Red Alert” 24/7 but that’s exactly what we do in cybersecurity…often without realizing it. What impact does that have an our approach? Our attitude? Our mental health?

A common step when you’re trying to get started in a career in cybersecurity is getting a basic certification. What comes after?

If you’re working by hand, you’re failing. In today’s world of security, rapid delivery, and new technologies, automation is critical.

Getting your first job in cybersecurity can be super frustrating. How can we work through traditional HR processes to get started?

There’s only upside to collaborating more deeply with other teams in the org. So why doesn’t the security get out there and do it?!?

We’ve spoken a lot of maintaining and expanding perspective when it comes to cybersecurity. In this episode, we dive in highlight a methodology called “service design thinking”.

Tanacon 1.0 was an unmitigated disaster. Not only is this a reminder that physical security is critical but it’s an example of a failure to analyze risk properly (or at all).

We (the IT community) don’t push for cultural change because it requires persistent and dedicated long term work. That runs counter to the usual pace of technology. We (the security community) are even worse off…

How new technologies are used and built is really up to us. Regardless of your moral compass, it’s important that you discuss the creation & use of these tools with your teams and larger community.

Getting started in cybersecurity can be hard. Sticking to core principles is critical as technology will change. But one of the hardest aspects to cultivate is perspective. How can you tackle that challenge?

Cryptocurrency is a digital asset. As such, it’s a major target for cybercriminals. We’ve seen attack after attack in the past few months as exchanges, apps, and other players in the cryptocurrency market aren’t aligning their security to the threats they face.

The DevOps movement is the single biggest opportunity security teams have had in a long time. The goal of DevOps is speed and innovation. That goal can be achieved with systems and automation: why not fully integrate security at the same time for a win-win?

We know that cybersecurity isn’t the best name to describe what is ostensibly, “information security” but it’s the name we’re stuck with.

Is it just attitude that keeps security teams from working well with the rest of the organization? And if so, can that attitude be changed? What’s keeping things so negative. Some thoughts…

At some point in the past few years, the term “information security” took a back seat to “cybersecurity”. Does it matter? Why?

Most of the focus around cybersecurity education is on the technical aspects. Is that the right approach?

I am often asked what a good undergraduate program is to take if someone is aiming for a career in cybersecurity. There are plenty of fantastic options but ironically, one I’m not a fan of is an undergraduate focused purely on cybersecurity!

GDPR comes into effect tomorrow and one of it’s biggest advantages is how it will force companies to actually manage their data…well at least personally identifiable information.

Apparently the FBI misrepresented the number of devices they can’t access due to encryption by up to a factor of 6x. This is most likely due to clerical error and a lack of actual statistics rather than malicious intent.

GDPR comes into effect on Friday, 25-May. What does it mean globally? Um…we’re not really sure.

Listening to customers is built into the DNA of a lot of organizations…why aren’t security teams doing the same?

Deep thoughts in this episode around ethics in technology and their use. Sparked by the latest issues around mobile phone tracking, this episode tackles the lack of ethics discussions around security and technology.

How can you create a break for yourself to get started on a cybersecurity career path? A few thoughts…

Getting started in cybersecurity isn’t as hard as you think. There’s no “ONE” path but there are a few key attributes that’ll make it easier.

There have been a lot of advancements in AI research and use lately, but are we moving in the right direction? Are we having the right conversations around AIs impact?

In this episode, I speak to the challenges around today’s cybersecurity and what that means for those just starting down the cybersecurity path.

Passwords are the best of a mountain of bad solutions. Picking a strong password lies at the intersection of math (yay!) and psychology…that’s a tough place to be. Here are a few tips on creating a useful, strong password.

Gmail just launched a nice, new redesigned UI. It’s slick and has some great new features. One feature, “Confidential Mode”, is particularly interesting and poorly named/positioned.

Can new technology solve everything? We in the security community need to spend more time investing in people and process.

Is IP blocking still effective? Is it a sledge hammer when you really need a scalpel?

Cybersecurity is often positioned from the negative. There are bad things coming to get you! What a waste of energy…

Encryption on mobile devices is a challenge for law enforcement. 3rd party companies often use hacks in their products to address this need. Is it right? Is it sustainable?

It’s often stated that you have to trade usability for security. I call 💩

CPU Vulnerabilities Seem Like A Massive Problem. Are they deserving of the hype?

One of the biggest challenges in cybersecurity today is the tendency to secure components instead of the larger system. It’s understandable but also leaves a lot of gaps. How can we change this approach?

Rumours swirl ahead of a new Canadian federal budget. Will they address cybersecurity?

Security awareness is next to useless. Educate users instead

Good data drives good decisions. This is a major problem in cybersecurity where the data simply isn’t available or accurate.

Ransomware is the scourge of the digital world. Cybercriminals are making money hand over fist. What can you do to protect yourself?

When you hide a message inside of another message, it’s called steganography. While you might not have known it’s name, this technique has a long and colourful history and it is still used today by cybercriminals.

Why do all incident response communications from customers feel the same? Why do they all miss the mark? How hard is it to do better?

Shellshock is a surprising bug. Hidden for decades, what do you need to know to help your organization respond?

Cloud computing is more than just fast self-service of virtual infrastructure. Developers and admins are looking for ways to provision and manage at scale.

If you strip away a lot of security terminology, it’s really about understanding what’s going on. If you want slap a fancy term back on, let’s call that “situational awareness”
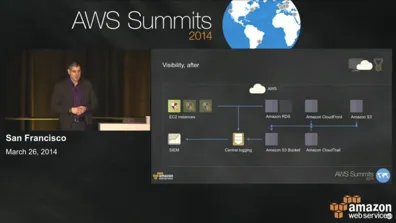
As AWS opened their summit series for 2014, 5000+ people packed into the Moscone Center. There was a ton of energy in the air and I got to talk about updating security operations for the cloud.

What does a modern security practice look like in the cloud? How do each of the area change?

Forensics is an area that’s often lacking in corporate environments. Few people have time to truly dig into an incident after it’s been resolved. Can we make forensics easier in the cloud?

Network security monitoring is changing dramatically in the cloud as more and more responsibilities are shifted to the Cloud Service Provider. How should your team adjust?

Incident response is often overlooked by everyone outside of the security team. In the cloud, automation and cooperation reign supreme.
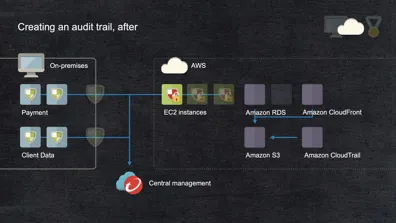
The cloud is a fantastic opportunity to improve your security posture…but only if you update how you handle operations.
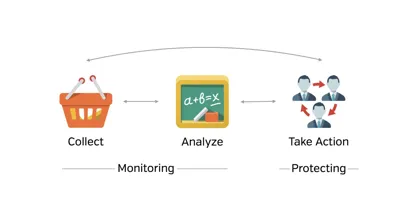
The cloud security discussion has changed from ‘should we’ to ‘how do we’. Here are the top issues you should be tackling.

When speaking to security issues in the media, what’s the right level of technical depth?

This post provides information that is designed to help you defend against phishing, spear phishing, and whaling attacks. Exploring the reasons for phishing, spear phishing, and whaling success