In my last post, I highlighted the lack of sharing in the information security community around best practices and discussed the ups and downs of operating security in hybrid and full cloud environments. I wrapped that post up with a call to arms of sorts but also a promise to help kick things off.
Incident Response
When it comes to defence, most teams focus on incident response (IR) processes. A very common approach is to adopt the SANS Incident Response Process. At a high level, this process defines six stages for incident response:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned
I prefer to visualize the process as shown below. In the midst of a response, the identification, containment, and eradication steps are usually cyclical as you discover more and more around the incident.
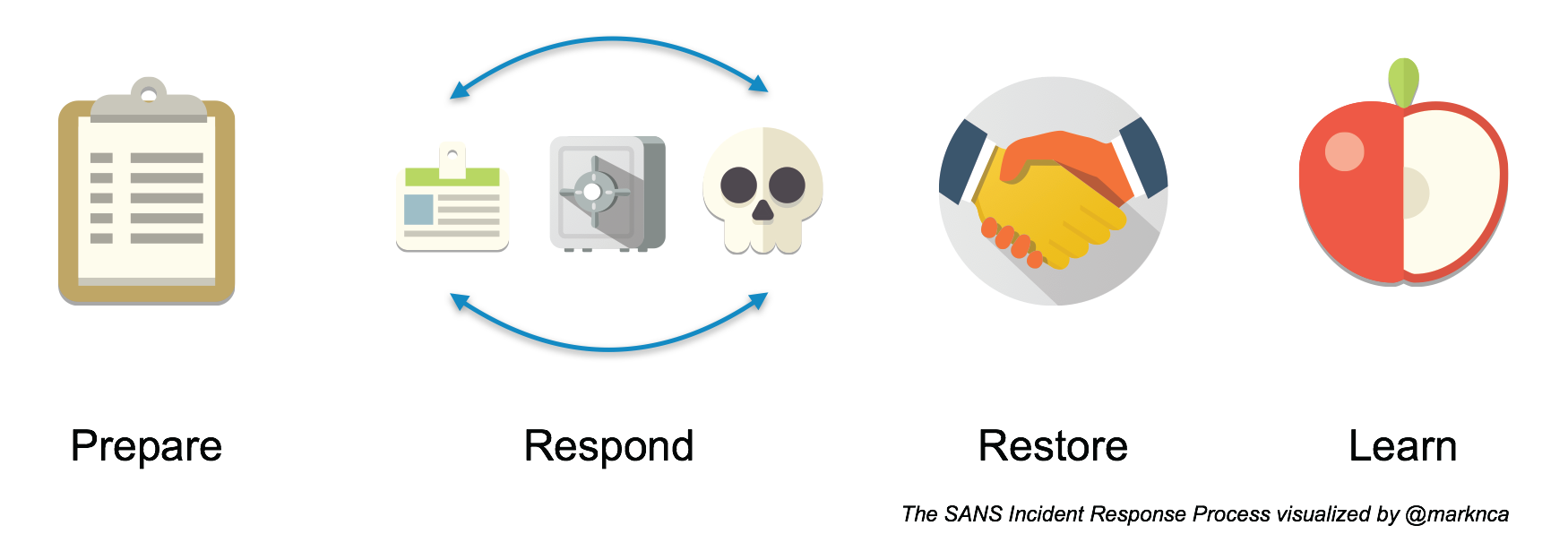
Please feel free to share this; it’s licensed BY-NC-SA.
Let’s keep this in mind as we explore what changes in hybrid and cloud environments.
Including A Cloud
The good news here is that this process, while defined for a traditional environment, is still 100% applicable to a hybrid or full cloud environment.
What is going to change are the steps we take in each phase.
Incident response is a huge topic; for this post, we’re going to focus on the preparation and recovery phases.
Preparation
The preparation phase is all about getting your ducks in a row. Do you know who you need to communicate with in the event of an incident? Do responders have the tools they need if the network is down? Is the escalation process clearly defined for everyone involved?
With the move to the cloud, the primary change for this phase is that your provider now has to be part of this loop.
If your provider hasn’t already published a process of how and when to get in touch with them for security incidents, reach out. Start that conversation.
When you’re under pressure of an incident and trying to restore production services, the last thing you want to be doing is trying to figure out who you need to speak to.
Add this information to your communications list. It’s critical that it be readily available.
Recovery
Recovery is often overlooked by the security team. It usually falls to operations to implement once given the “all clear” from security.
But when we move to the cloud, new opportunities open up for us. We now have the ability to short circuit the identification, containment, and eradication phases. Yes, we still need to conduct the activities in these phases, but we can restore production services almost immediately in some cases.
Take, for example, a report of malware on one of your production web servers. In a traditional environment, you would:
- Remove the server from the network (and thus, production) 2a. In a virtualized environment, start the process to create a new server to take its place 2b. In a physical environment, start to panic
- Analyze the infected server to identify the malware
- Evaluate the effect of the malware on your network
- Clean (eradicate) the malware if possible, rebuild the server if not
- Add custom defences to prevent further infection
- Restore production to full capacity
Now, if we truly embrace the cloud and fully leverage its capabilities, we can:
- Isolate the instance for later analysis
- Instantiate a new instance to restore production
This process should take just a few minutes and be completely automated. That means in parallel, we can:
- Analyze the infected server to identify the malware
- Evaluate the effect of the malware on your network
- Terminate the infected instance
- Add custom defences to prevent further infection
The tactics we can use in the cloud reduce the impact to our business, which–as a security practice–is our #1 goal!
It also relieves the stress on the response team. With production at full capacity, the team has more time to properly evaluate the infection, its impact, and work on new methods to prevent further infection.
What’s Next?
In this post, we’ve glimpsed at what changes we can expect and work toward as we move security operations to hybrid and full cloud environments. This is just the tip of the iceberg. What advantages have you seen moving to the cloud?
Please add you thoughts in the comments below or on Twitter (where I’m @marknca). Let’s work together to help ensure that everyone can increase their level of security in these environments.