Originally presented at ServerlessConf in NYC on 08-Oct-2019.
Cybersecurity is topic that comes up regularly as something you have to do…or should do…or are forced to look at by your security team. But why? There have been reports of serverless threats. Rumours of traditional security issues that should keep you up at night. Is any of it real?
When new technologies are adopted, cybersecurity implementations follow the same pattern. New innovations allow developers to move faster, operations gets onboard, and then security swoops in armed with a mountain of fear, uncertainty, and doubt.
We can do better.
Serverless is an unprecedented opportunity to modernize our approach to security. In this talk, we’ll look at how we can accomplish this and build strong solutions without the FUD.
Slides

When I was younger, I was convinced that the world would end in flames.

The year was 1983.

I was 5 at the time.
👈 Yes, that's actually me. And yes, I'm rocking that sweater/turtleneck combo.
Regardless, I was convinced the world was about to end a fiery death. In retrospect, I may have had some issues—still do. But if we look back at that little boy's world view, is it so crazy?

Despite my obvious bias, I don't think it is. I think that thinking the world was going to burn was a completely reasonable conclusion to draw given the information provided.
Or more accurately, the individual take away from the various information provided.

What does a childhood fear in 1983 have to do with serverless security in 2019?
That's what we are going to explore in the rest of this talk.

Before we get started though, let's re-visit 1983 (briefly) and get a feel for what was happening...besides that sweater I was rocking 😉.

McDonald's introduced the Chicken McNugget for the first time ever. No word yet if they just made one giant batch of the pink gooey stuff in 1983 and are riding that out until about 2050 when they finally have to make a second batch.
Mario Bros was released in the arcade in Japan. Miyamoto-san and Yokoi-san re-introduce Mario the plumber from Donkey Kong kicking off an unprecedented, world-wide phenomenon. The game is not a hit in arcades but receives a 1up on the new wave of home consoles.
His brother, I-look-like-you-but-in-green-just-to-save-memory-Luigi, is also introduced...if anyone cares about that.

The space shuttle (remember those?) Challenger flies mission STS-7. Over 6 days, the conduct a number of experiments and deploy two satellites.
This mission is also the first for American astronaut, Sally Ride, making her the first American woman to fly in space.

The Cold War is still on. Mikhail Gorbachev won't rise to power for another two years. In this pre-glasnost era, tensions are high.
Events throughout the year combine to keep those tensions high. It'll take another six years for the Berlin Wall to fall...

The Baseline

So what in the mind of a 5 year could possibly lead to the conclusion that the world was about to end in flames? 🔥
To truly understand that, you need to know a little bit more about me...
I'm a military brat. My father eventually served for 33 years and at this point in my life, I had only ever lived on base.
This means that nearly every adult in my life was either in the military or directly supporting someone who was.

And like any young boy, I was intensely curious as to what my father did while he wasn't at home. At this point in his career, he was a navigator flying the Canadair CP-107 Argus.
As a navigator, he was often away on mission for a few days at a time. Given the squadron rotation, this meant it was either his crew or my friends parents that were away constantly.
When I asked what they were doing flying around so much, the answer was both cool and scary.

They were hunting Soviet submarines.
Apparently, the Soviets would sail missions throughout the pacific gathering intelligence and keeping their armament mobile.
Five year old translation filter: enemies are all around us hiding in the ocean. The same one you play in while we're at the beach on weekends.

These facts, process through a growing mind ended up with as the following foundational pillars:
- Enemies are working against us
- We are under constant threat
- Everyone is worried
* I feel at this point, it's really important to point out that I had a wonderful childhood. My parents loved me (and—ugh—my big sister 😉). We were objectively quite safe and never went hungry. My experiences growing up on base were actually quite unique and a lot of fun.
Double that if my parents ever read this 💖. And if my sister does 😜.

The Environment

If that was the situation that was working to shape my young mind, what about the greater environment? What was happening in the world in 1983 that lead me to that fiery conclusion?
Missiles. It was mainly missiles.
Intercontinental ballistic missiles or ICBMs were a major topic on the news, in magazines, in the papers.
The question at the time was how many minutes would it take before a missile launch triggers "mutually assured destruction". Was it going to take 20 minutes...or less?

In response to this constant threat, President Regan proposed the Strategic Defense Initiative or SDI.
At it's heart, this was an anti-missile defence system that used both ground and satellite-based installations in order protect the United States and it's allies against Soviet aggression.
The initiative was also designed to boost military R&D as it promised a number of things that simply didn't exist at the time. Things like particle beam weapons.

As the media started discussing the initiative, it was quickly dubbed "Star Wars". This was something that five year-old me knew well.
I lived in a small town. That meant that even though Return of the Jedi was released in 1983, it wasn't at the local theater for quite a while.
What did come to the local cinema was a double feature of Star Wars and The Empire Strikes Back. My father took me to see both of the movies. He promptly fell asleep but I was riveted.
The problem? At the end of Empire, Darth Vader is winning.

These external factors create an environment that can be summed up as:
- The cold war doesn't feel so cold
- ICBMs could launch at any time
- Darth Vader is coming

The Threat

Despite the omnious setup so far, this isn't enough to convince a little boy that the world is about to end in flames 🔥 (it's close though).
The triggering event was actually completely innocuous.
One day while waiting for my sister's skating lesson to finish, I was sitting in the car with my mom. We were listening to the radio, just a typical Saturday afternoon show.
This episode featured an astronomer from a University somewhere and he was talking about a new find...

This is an interesting find for the scientific community and it's proximity to earth offers a unique chance to study it.
Given the positive side of the Star Wars focus, the ongoing shuttle missions, space is hot right now. One thing that hasn't changed (forever) is that academics will take any opportunity to promote their field of study with the great populace (and they should!).

The problem? 3200 Phaethon is classified as a "potentially hazardous asteroid" because it's too close to our planet.
It's important to call out here that "too close" in an astronomer's galactic view does not align with the majority of the population.
Too close? Yes, it's just 0.01945 AU away.
That works out to 2,910,000 km from our planet. But the journalist is curious and asks the reasonable follow-up, if 3200 Phaethon hit Earth what would happen?
Given it's size (5.8 km), probable mass, and current speed. If the vector changed and it hit Earth, it would create a crater about 120 km wide and the aftermath would wipe out most—if not all—life on the planet.
Oh. Five year old me forgets everything else during the segment.

The takeaways from the unexpected-but-completely-connected-in-my-young-mind threat:
- This Potentially Hazardous Asteroid is a hairs breadth from Earth
- It's impact would be devastating, easily taking out a city and most of the surrounding area
- After impact, every dies slowly and painfully

1983: Not so great.
* Again as a caveat: I really did have a great childhood.

But like it is for any child, at times the world is hard to understand and you draw conclusions that aren't supported by the evidence if viewed in the proper context.
For five year old me, we have the baseline mental model, the larger environment, and a triggering threat.

This lead to my conclusion that the world was about to burn.
So what did I do?

I made a blanket fort in the basement and hid.
I've always felt comfortable in blanket forts and that feeling of safety made it easier to accept what I assumed was coming. It's a natural reaction.
When confronted with a impending terror, it's normal for humans to resort to what they know. Whether that makes sense or not.

Back to the present. What does this have to do with 2019?

Simple. Serverless architectures and services break existing security models and tools.
Real talk: cybersecurity defenders are barely hanging on. Wave after wave of threats are at the door and existing solutions are so complex that defenders are teetering on the edge.
Let's breakdown this situation down into the model we just used for five year old me.
It starts with that traditional approach to security...

The traditional security approach assumes that assets are long lived. The definitely of "long" has changed (begrudgingly) over the past few years with the normalization of cloud.
But fundamentally, traditional approaches assume assets existing for days, weeks, if not years.
On top of that, those assets are accessible.
Installing agents on the operating system, adjusting the routing tables in the network, being able to analyze memory dumps after an incident...the vast majority of cybersecurity defence assumes deep access.
The third baseline in traditional security is that—despite the hype—the perimeter is still king. Segmentation and access control are "reliable" staples for cybersecurity teams.

If that's the baseline, what is the external environment like for cybersecurity today in 2019?
The elevator pitch: defenders are losing ground.
Globally, we see an new malware variant approximately every 0.3 seconds. Those variants are usually mutations of existing samples though they can be entire novel as well.
These mutations are created to help avoid anti-malware systems as well as to obscure the trail left for the any threat hunters.
Adding to that challenge is that every 3 days a new vulnerability is published. Whether that vulnerability affects system in use at your organization needs to be determined. Then a risk assessment must be conducted and the appropriate remediation steps taken.
These are the fact that defenders know. Worse is the constant fear of what they don't know. What has slipped through their defences? What new threats are on the horizon?
Defenders can't keep up and they know it.
I have a lot more to say on why defenders can't keep up but that's a subject for other talks and videos.

The trigger for defenders in 2019? It's the threat of cybercriminals.
In 2018 alone, cybercriminals brought in an estimated $1.5T USD. It's hard to provide an exact measurement but this doesn't seem like a crazy number.
Worse, defenders spent about $4.5T USD recovering from cyberattacks. This number covers all the new equipment purchases post-breach, consulting fees, and lose revenue.
To put an emphasis on the point, there are very few convictions for cybercriminals. There are some system takedowns but usually that infrastructure comes back online in just a hours or days after a major takedown.

Defenders are not winning.

Their reaction? Hide.
Ok, well not hide exactly but the digital equivalent.

Defenders have reaction by falling back to old standards. They are trying to apply traditional security techniques to modern, serverless architectures.
That simply won't work...and not just because the areas where traditional security is applied are now the responsibility of the cloud service providers.
Don't get me wrong, the OWASP Top 10 for Serverless and the CSA 12 Most Critical Risks for Serverless Applications are good documents.
The problem is that they have a near myopic focus on the functions-as-a-service element of the design and they practically ignore all of the other aspects of these architectures.

So how do we come out from under the blanket fort?

The first step is to realize that despite the theoretical risks posed in the OWASP and CSA documents, there is a very real and very problematic issues facing everyone right now...
MISCONFIGURATIONS

Misconfiguring cloud service features is the #1 security issue facing builders today...by a ridiculously massive margin.
Look no further than the avalanche of headlines from the past 24 months citing organizations that have misconfigured cloud storage (typically Amazon S3) and needlessly exposed customer data.
THAT'S WITH A SERVICE WHERE EVERYTHING STARTS COMPLETELY LOCKED DOWN!
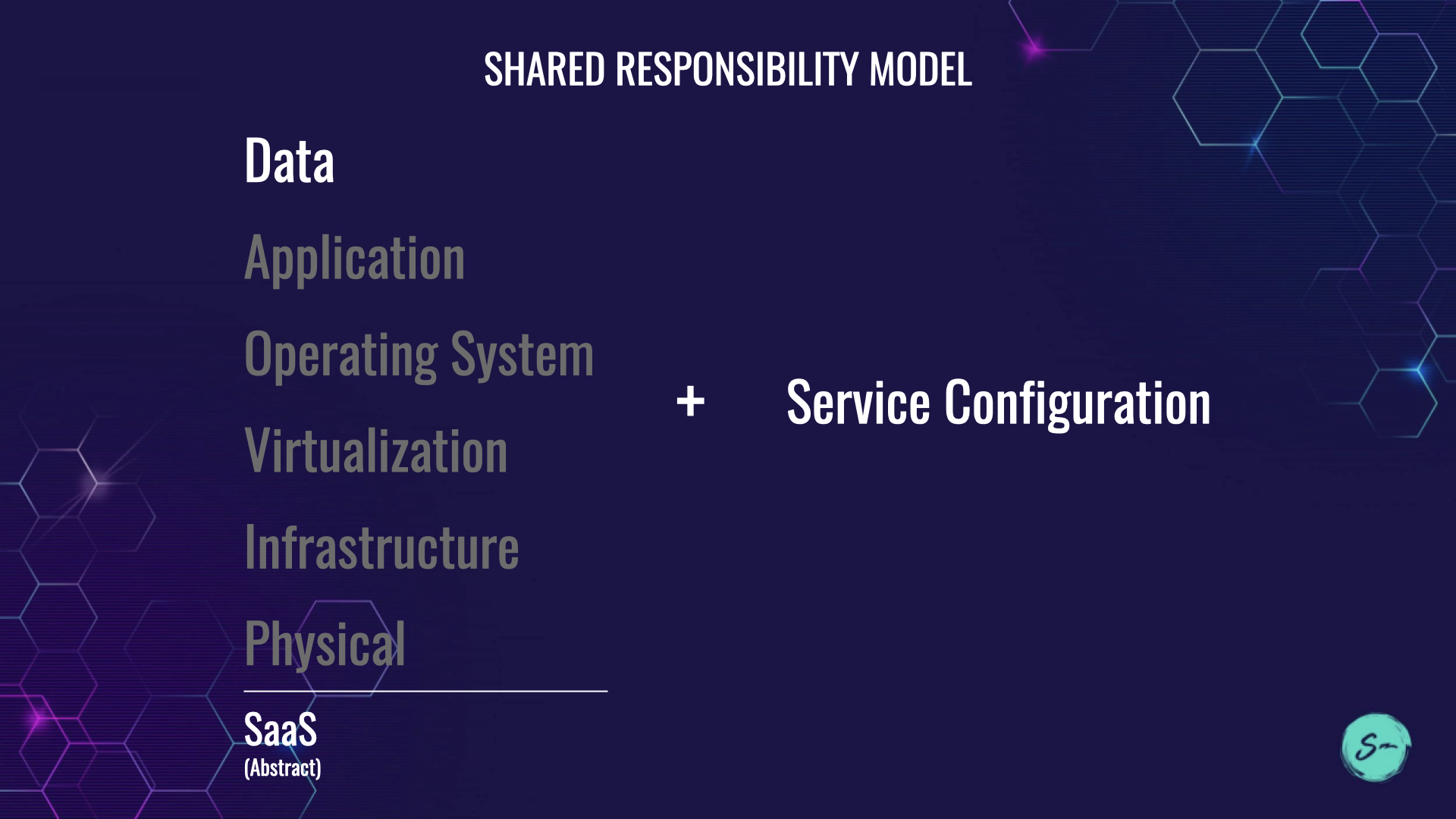
In the Shared Responsibility Model, with serverless applications you are responsible for your data (in the case of FaaS: your code is the data) and the configuration of the service you're using.

There are four pillars for serverless security. I used to position this as three but we obviously need to break "service configuration" out on it's own given the real issues we have and continue to see.
- Service selection: do the services you build your app from meet your business needs?
- Functions: is the code high quality?
- Data flow: is the data intact? Is access to that data controlled?
- Configuration validation: are the service features setup?

The goal of cybersecurity is simple.
Make sure that what you build works as intended...and only as intended.

Thank you!
