Originally presented at the Fast Company Innovation Festival 2019.
Technology is omnipresent in our lives. From the time you wake up and check the weather to the time your head hits the pillow, you will have spent at least a quarter of your day interacting with technology.
In this talk, Mark Nunnikhoven, vice president of Cloud Research of Trend Micro, will navigate you through your average 24 hours and uncover which privacy and security concerns are overblown, and shine a light on the unknowns that really should keep you up at night.
Slides

Technology is so complex that it’s easy to assume that we’re only a blink away from the robot apocalypse.
Don’t worry, we’re not there yet.

Really, we’re no where near the robot apocalypse (what exactly are you doing roboticists?)
...regardless of what you seen in the movies
...or what your uncle said
...or conspiracy theories
...or any of the major headlines you seen regularly

Movies love to show extremes. Cyber security and privacy issues aren’t visually compelling and are typically way too complex to show in any digestible form.
I’m a digital forensic scientist and my work is not what you see on NCIS or in movies like Blackhat. Those shows are way more entertaining but, they are just that...entertainment

Maybe you heard about how easy it is for hackers to get into systems from your uncle, or your neighbour, or your hair dressers nephew’s friend.
Playing telephone always distorts reality. Some vulnerabilities are easy to exploit, others are extremely difficult. More often than not, that big “hack” you heard about it is just someone guessing a password

Conspiracy theories abound. When it comes to cyber security, almost every hack is thought to be done by a rogue nation state.
When hacks hit the headlines, it’s human nature to try and figure out “who dunit”? It’s not useful, but it is human nature

And those headlines—like all headlines—aim to draw readers in. Big numbers, dramatic claims, anything that will pique a readers interest...usually something that stirs up a negative reaction
The reality of cyber security and privacy is much more complicated. It’s all of these things and none of them at once.
And that’s understandable, the technology we take for granted is astonishingly complex. It’s amazing it works at all...

What risks do you face every day? Are you even aware of them?
Let’s walk through a typical day and explore some of the issues that pop up...

07:15
It’s 7:15am and your day is just getting started...

Like most adults, you start the day by trying to learn about what’s going on in the world
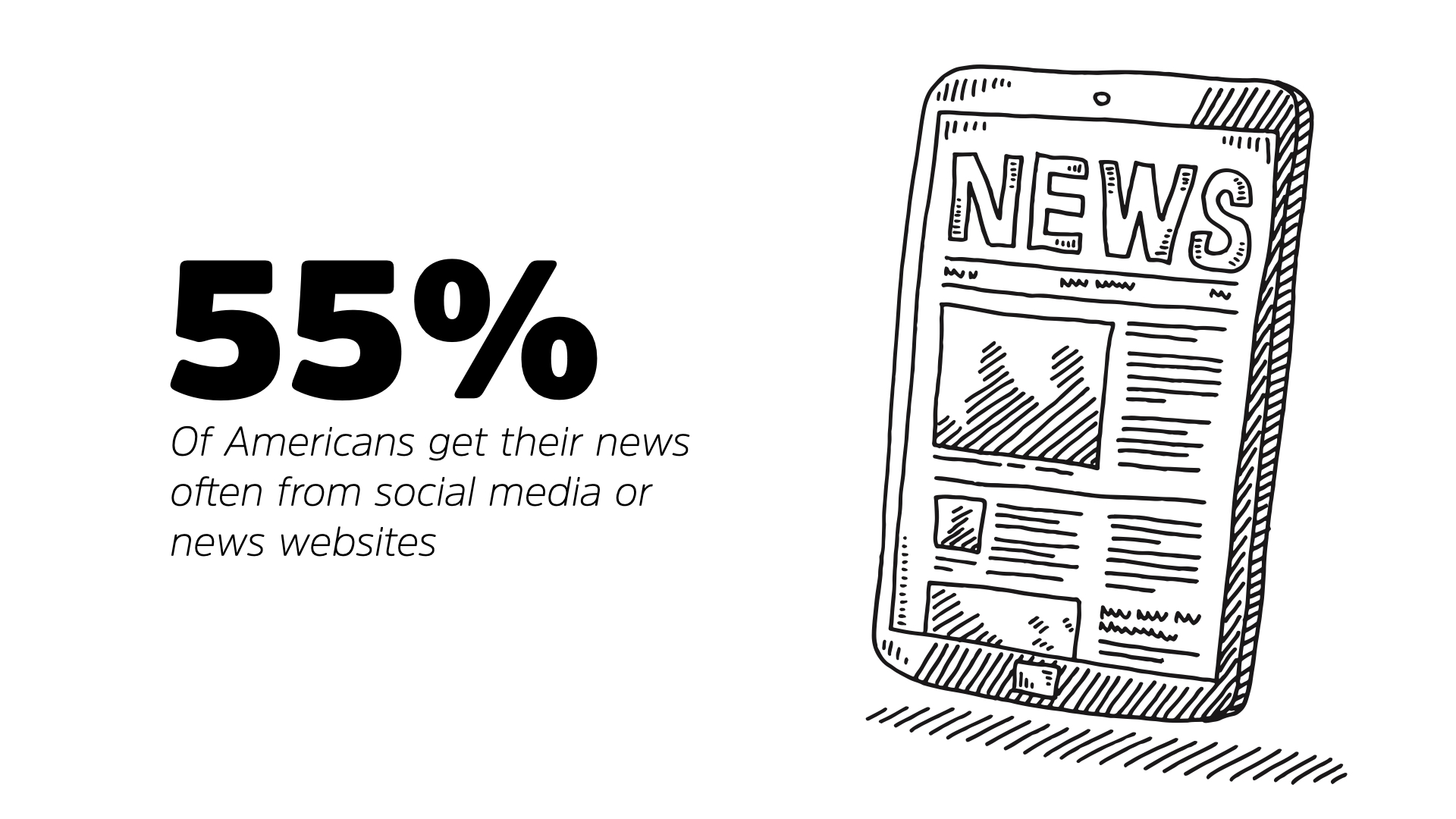
Whether that’s via social media or news sites, you are part of the 55% of Americans that get their news online
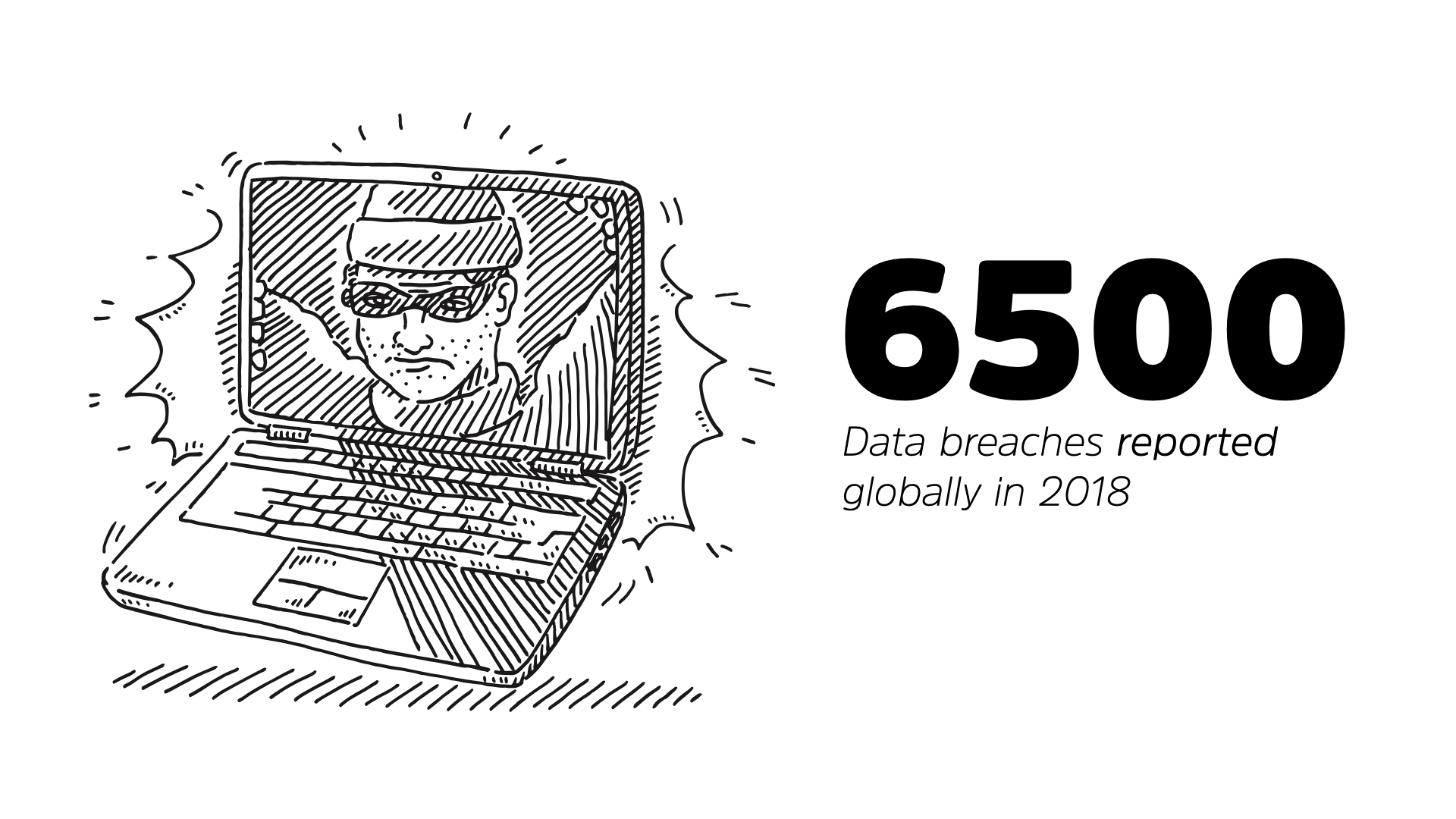
Odds are good that one of those stories your read in your feed is about a data breach. There were 6,500 breaches reported globally in 2018.
In the US, data breach reporting laws—and privacy laws in general—are a mess. Companies are not required to report all breaches and when they are, there is usually at 45 day window to make an initial report
BUT that data breach story isn’t the real problem. Most of the time, the data stolen is of little consequence to you as an individual.
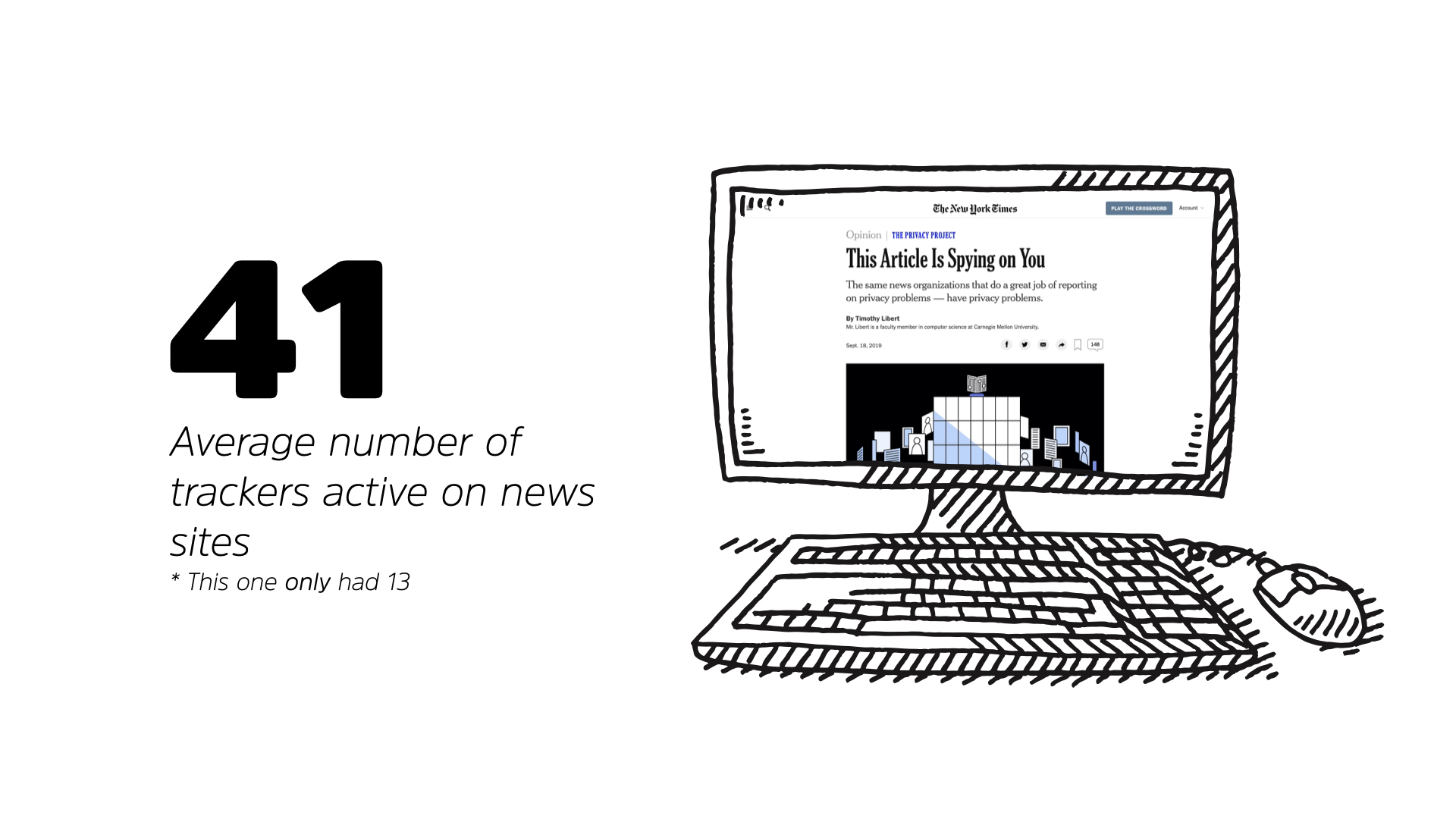
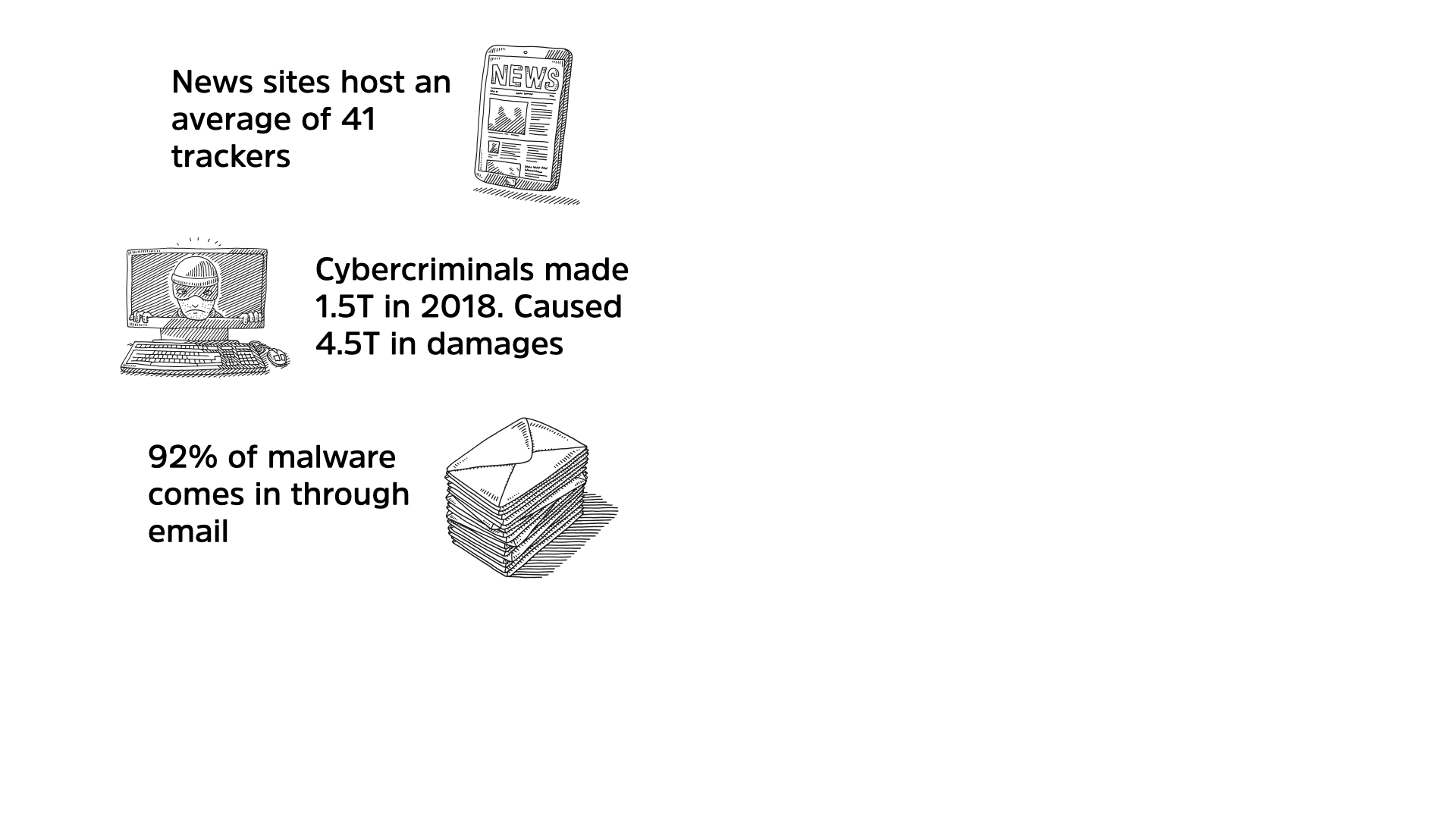
More troubling is the 41 different trackers that are active on that news site you read the story on. These trackers follow you around the web creating a nuanced profile of your behaviour that companies use to target advertisements and customize products to better draw you in

10:30
It’s 10:30 am and now you’re in the office (even if that’s a coffee shop)...
Your mind wanders a bit still thinking about that news article you read this morning on a massive data breach. By now, you’ve probably seen an uptick in targeted advertising but haven’t really connected the dots on why you’re seeing more specific ads.
What you are thinking about is how these nation states keep hacking companies in order to get at your data. It’s always Russia or China, right? They want all of our data?

The answer is much simpler. In 2018, it’s estimated—because criminals aren’t great with earnings reports or taxes—that cybercriminals made $1.5T USD from their activities.
That’s from selling stolen data, direct ransoms, selling services to other cybercriminals, and a number of other services

In addition, cybercriminals caused about $4.5T USD in damages to organizations around the world in 2018.
This money was spent on data recovery efforts, incident response, security audits, new equipments, etc. While not ending up in criminals pockets, these costs have a very real impact on the victims

Do these cybercriminals use state of the art hacks (zero days) to access our systems? Nope.
Email accounts for 92% of all malware. Delivered either directly as an attachment or as a link that you click on. Email continues to be an extremely effective route into your networks

Take this link for example. Is it legitimate? How do you know?
Any security training you’ve taken has taught you how to look at a link and tell if it’s malicious. So, is this link malicious?
* It’s not btw, it’s a marketing link...so maybe it’s malicious? Seriously though, the same security teams that tell you to look at a link and determine whether or not it’s safe, work for companies that send out marketing links just like this one!
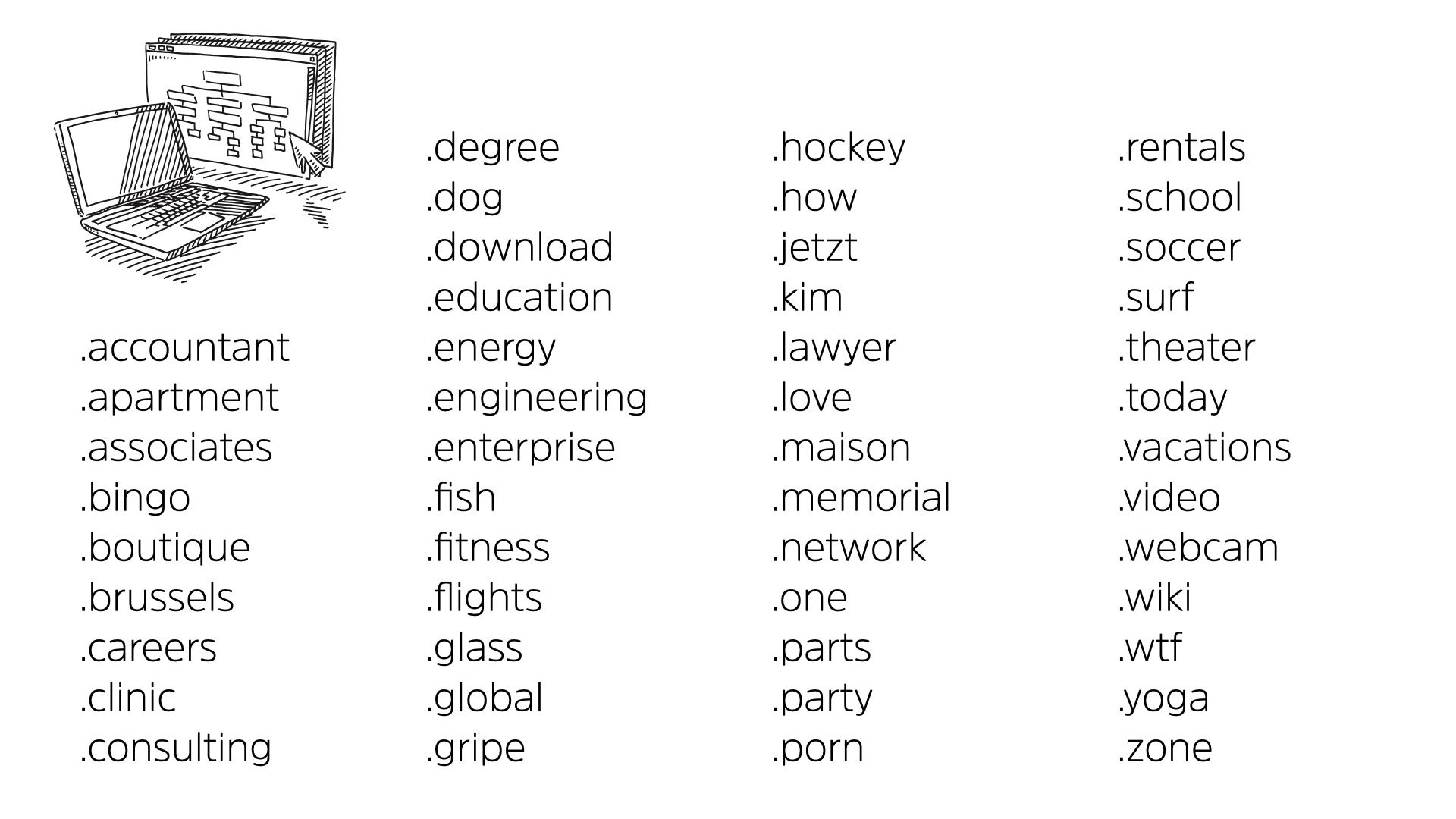
Here’s another pop quiz. Which one of these top level domains is fake?
The only ways of “protecting” yourself in email simply don’t work. The only reasonable way forward is to use a security control to check links (usually done on the server) and when a link asks you to take an action...think twice, then think again

12:15
Moving into lunch time, what does our day have in store for us now?

Let’s say we head to our favourite local eatery. You have a nice meal and pay with a credit card.
The server takes the card and rings it through, returning with a bill for you to sign

You may be thinking that credit theft is a serious problem (it is) and that you should be worried about it...and you wouldn’t be wrong.
But identity theft is far more serious. As long as you haven’t done anything egregious, you’re protected from credit card theft

Identity theft is much hard to detect and recover from. In the US alone, impostor scams took in $488M USD. Many of these scams start online but capturing credit card details is a strong first step as well.
With that foothold into your identity, criminals can start to leverage other data points to get government issued ID or a bank account in your name and then really do some damage to your identity
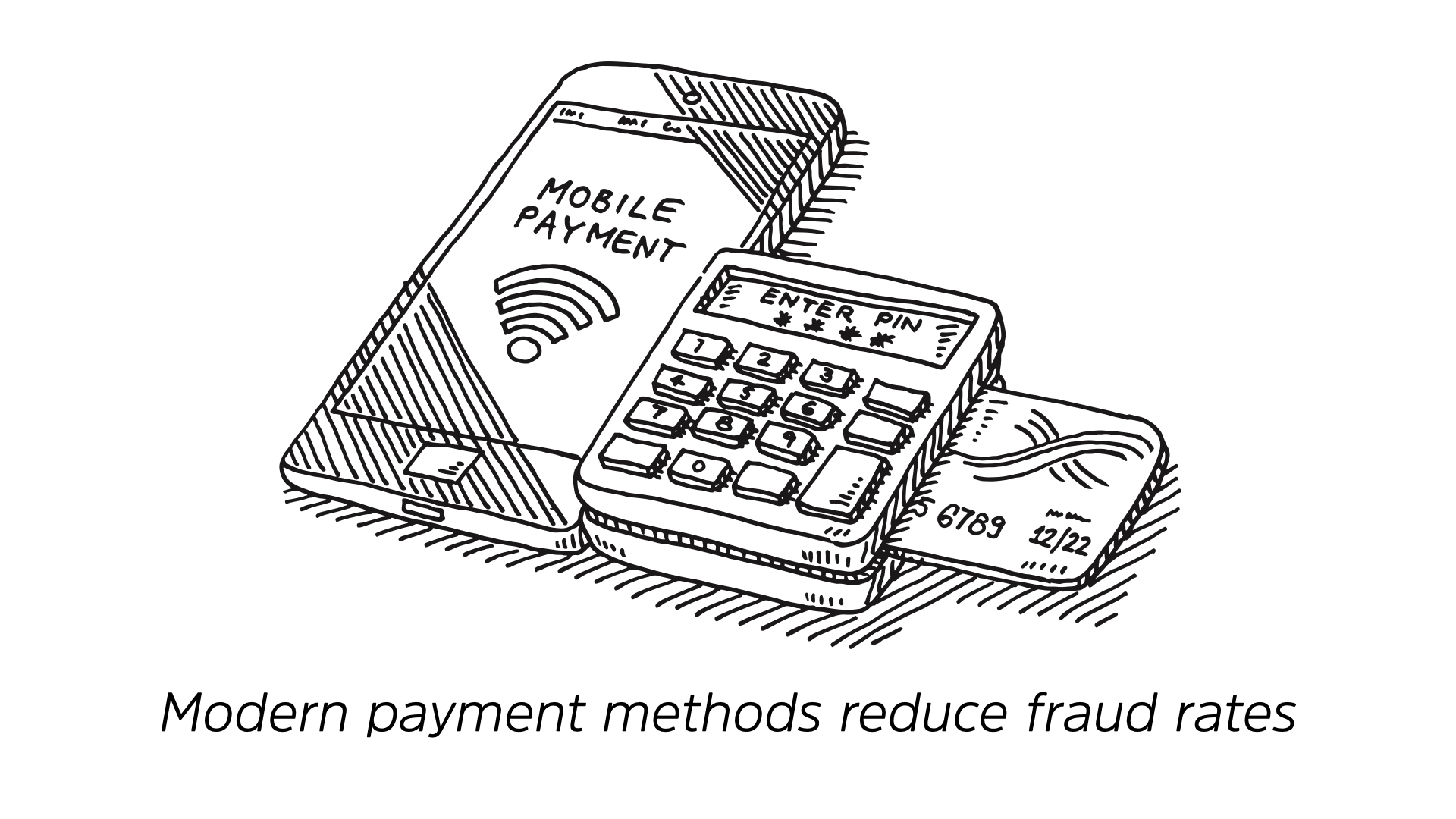
Modern payment methods like chip-and-pin and Apple/Google Pay can reduce the chances of your credit information being stolen and used as a first step in an impostor scam.
Chip-and-pin protects your physical card by reducing the impact of losing that card or having it cloned. Apple/Google Pay actually generate a new card number for every transaction, making stealing your financial information extremely difficult

14:30
Let’s slide into the afternoon now...

Perhaps you decide to come see a talk at a festival or conference.
While you’re there, you want to connect with the world and share what you’re experiencing on social (#FCFestival)
But who is running that wifi network? What are the terms of service on that network? Is that network being actively monitored?
Is that a risk?
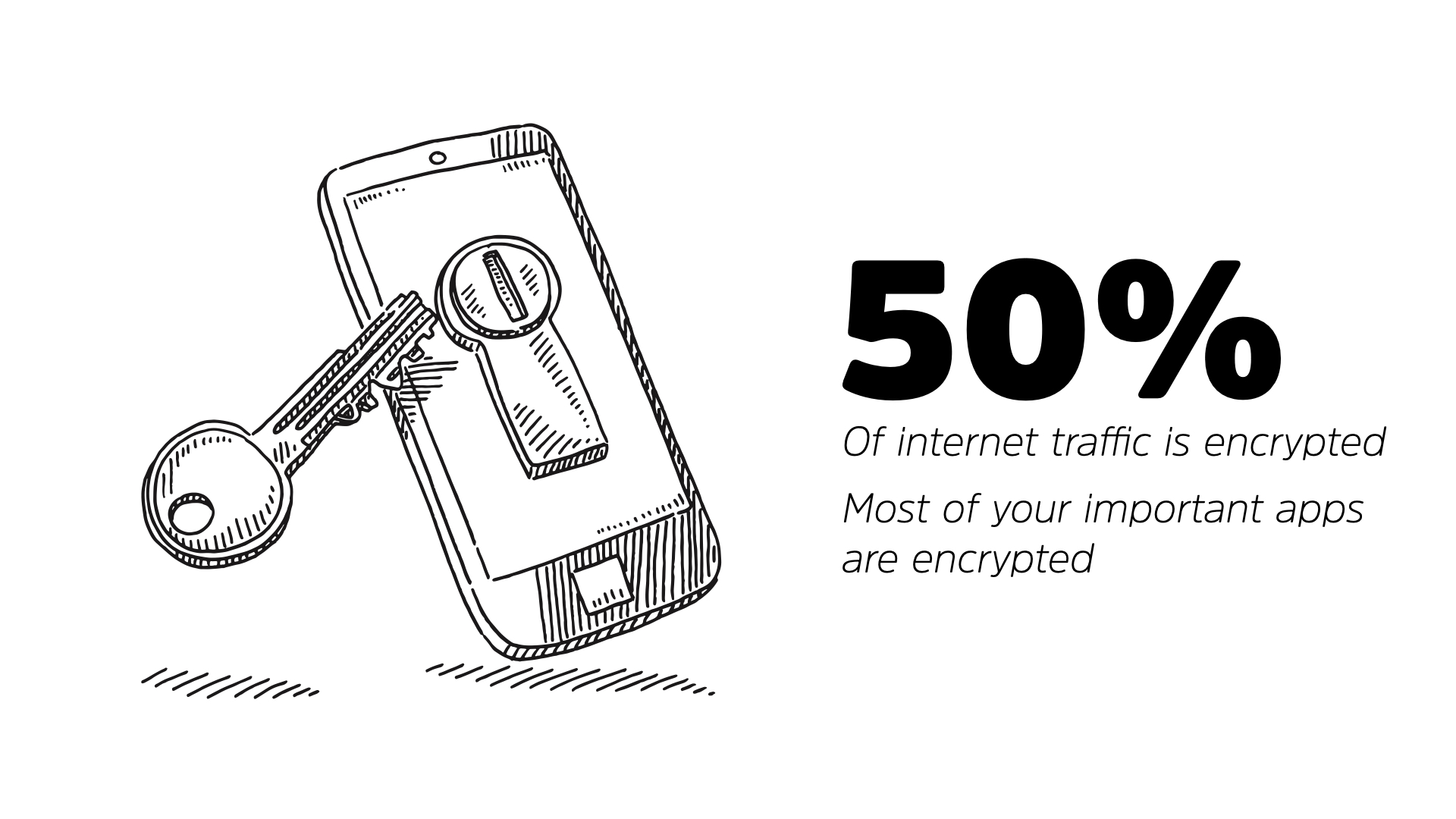
Yes, it’s a risk. Wifi works like a bubble around you. Anyone else in that bubble can access your traffic. That’s why individual connections are encrypted (but that encryption browser easier to break with longer connections).
The good news here? Around 50% of your internet traffic is directly encrypted. That “S” in HTTPS or the little browser padlock is working to protect your traffic
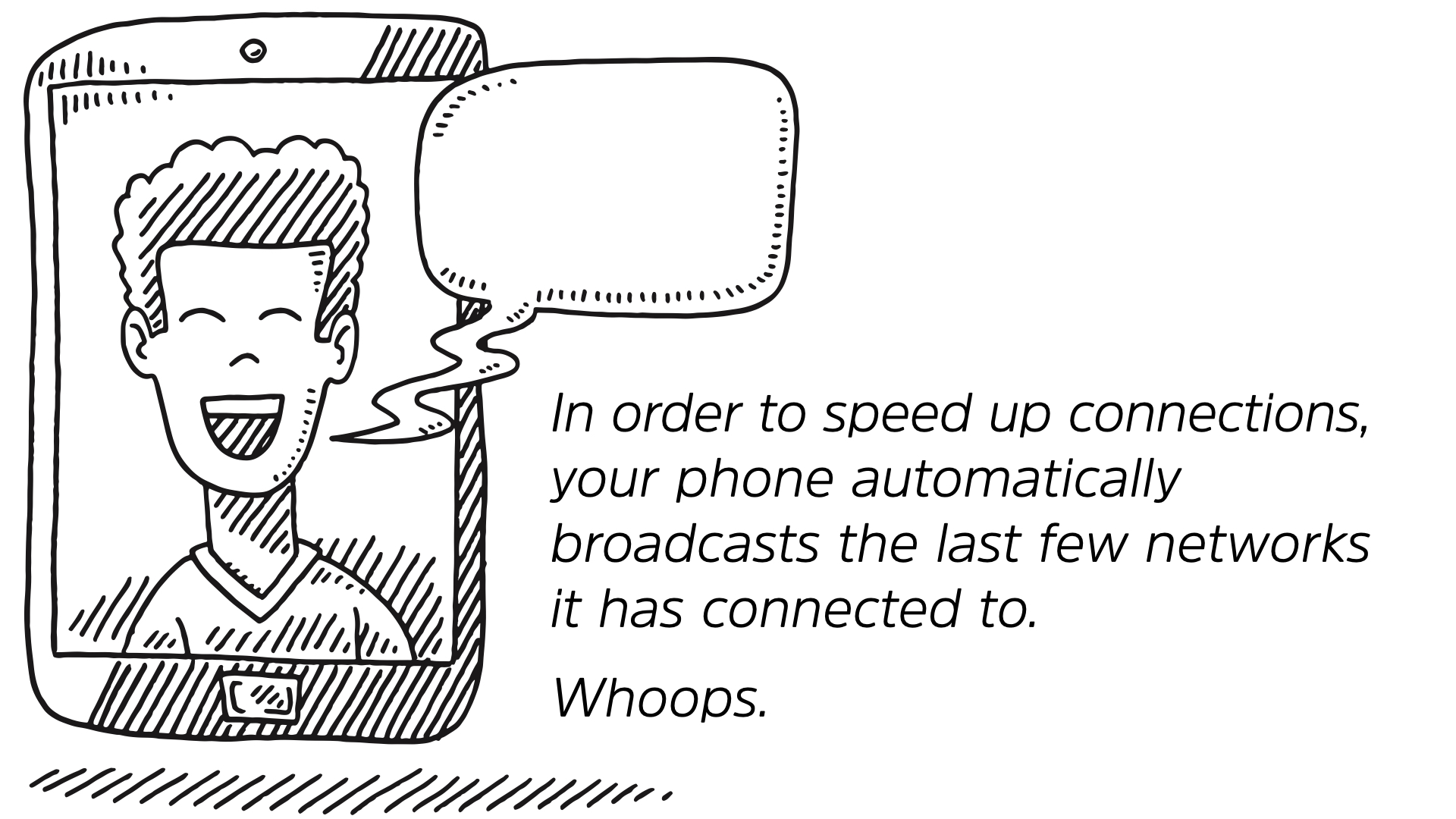
What is more directly impactful to your privacy is that your phone broadcasts the last few networks it has been connected to in order to speed up reconnections to wifi.
So if you visited the office, Starbucks, and your friends house because you came here, the phone told everyone that when you walked in the room

18:00
We’ve reached the end of the work day and it’s time for you to leave the city or at least the core and return home
That commute has a lot of interesting data points in of itself. For arguments sake, let’s say you live in one of the areas where self-driving ride hailing apps are a thing. Or maybe your car is nearly self-driving on it’s own. Tesla is almost there, it’s not that far off
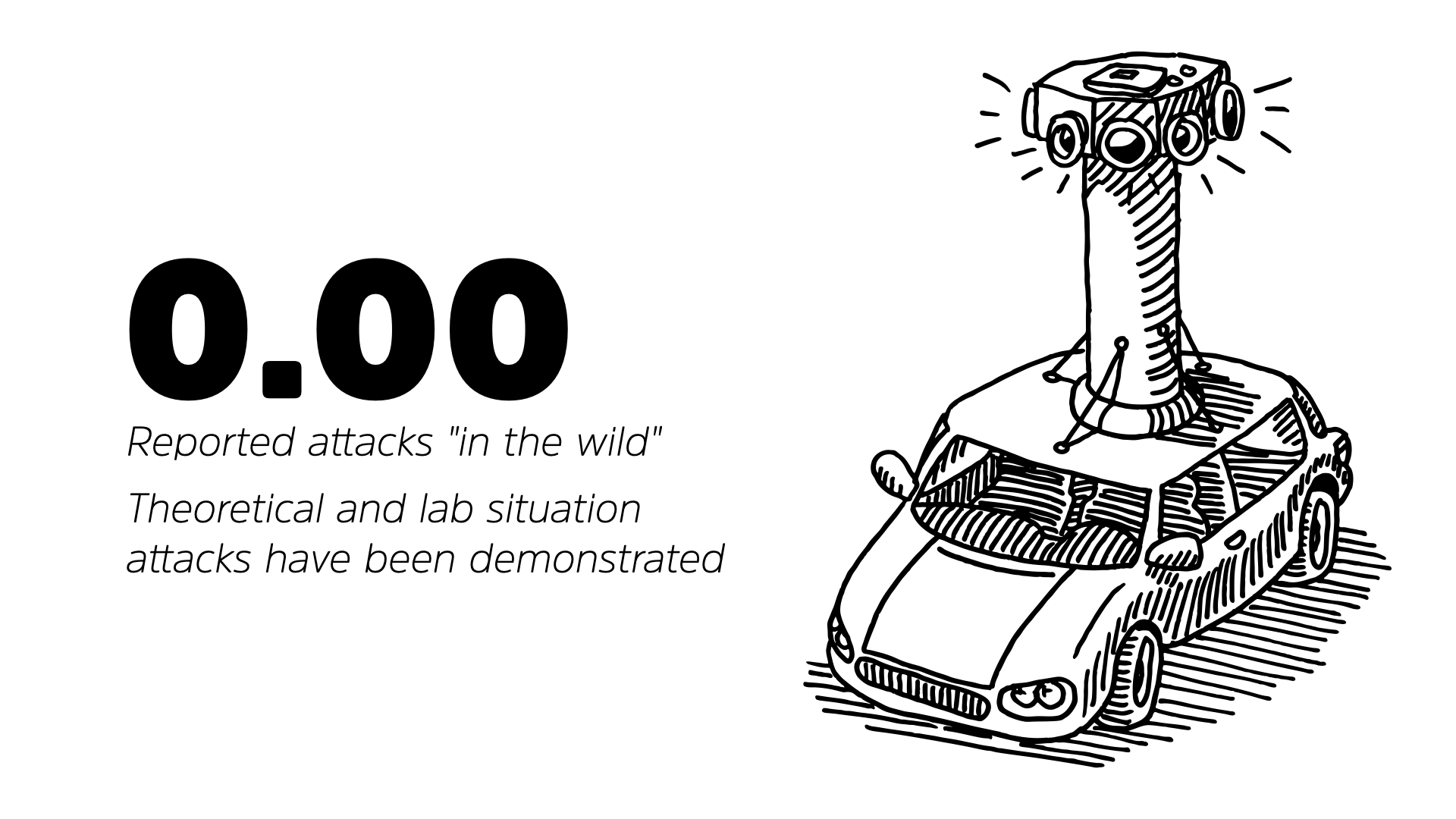
There is legitimate concern about the viability of attacking smart cars. Whether or not they are self-driving. We’ve seen demonstrations of attacks where hackers gain entry to cars seamlessly. We’ve even seen them shut down vehicles remotely while the vehicle was in motion. But there have been ZERO confirmed attacks in the “wild.”
That’s not surprising given the main network in our vehicles was designed in 1986. Lot’s to dig in there but let’s push that aside for now. What’s about the A.I. side of smart cars?
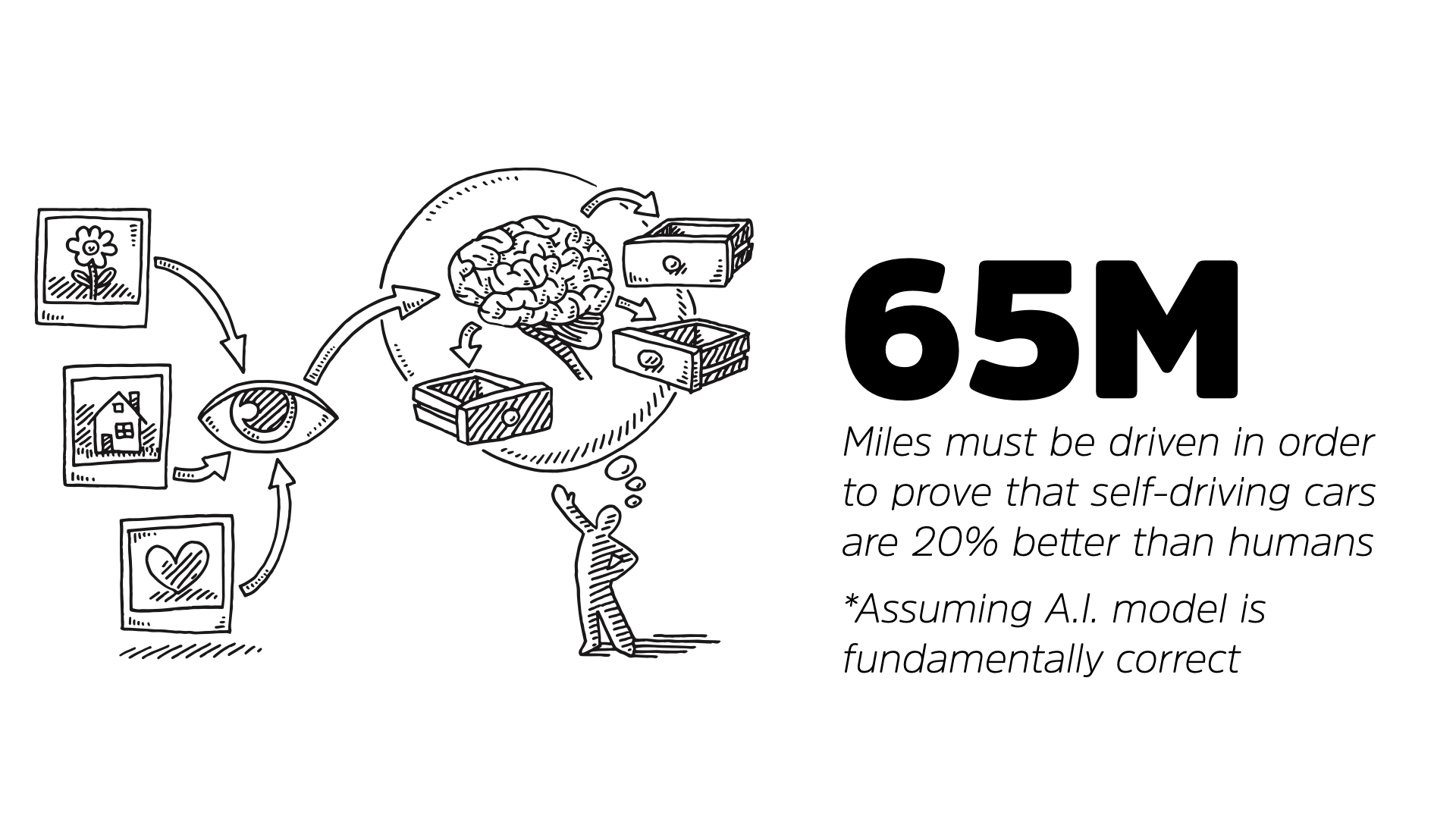
A recent study found that 65 million miles would have be driven by self-driving cars in order to prove that there are 20% better than human drivers. That’ll take about 3 years 24/7. There is real (and valid) concern about self-driving cars but the major concern is the model which we need to explicitly program into them.
When faced with an unthinkable choice, humans will react in the moment on instinct. Self-driving cars will have been pre-programmed with a decision tree. What does that look like?

20:00
You’ve finally made it home (safely!) and it’s time to unwind
Odds are you’re one of the 67% of Americans that play video games in one form or another.
Let’s say you’re a big gamer and you log into your favourite network to play with friends online.

51% of people use the same password for their personal accounts that they do for their work ones.
There have been numerous game services and networks breached in the past few years with millions of user credentials exposed

That’s a big problem given that 57% of people don’t change their passwords even after an event like being phished
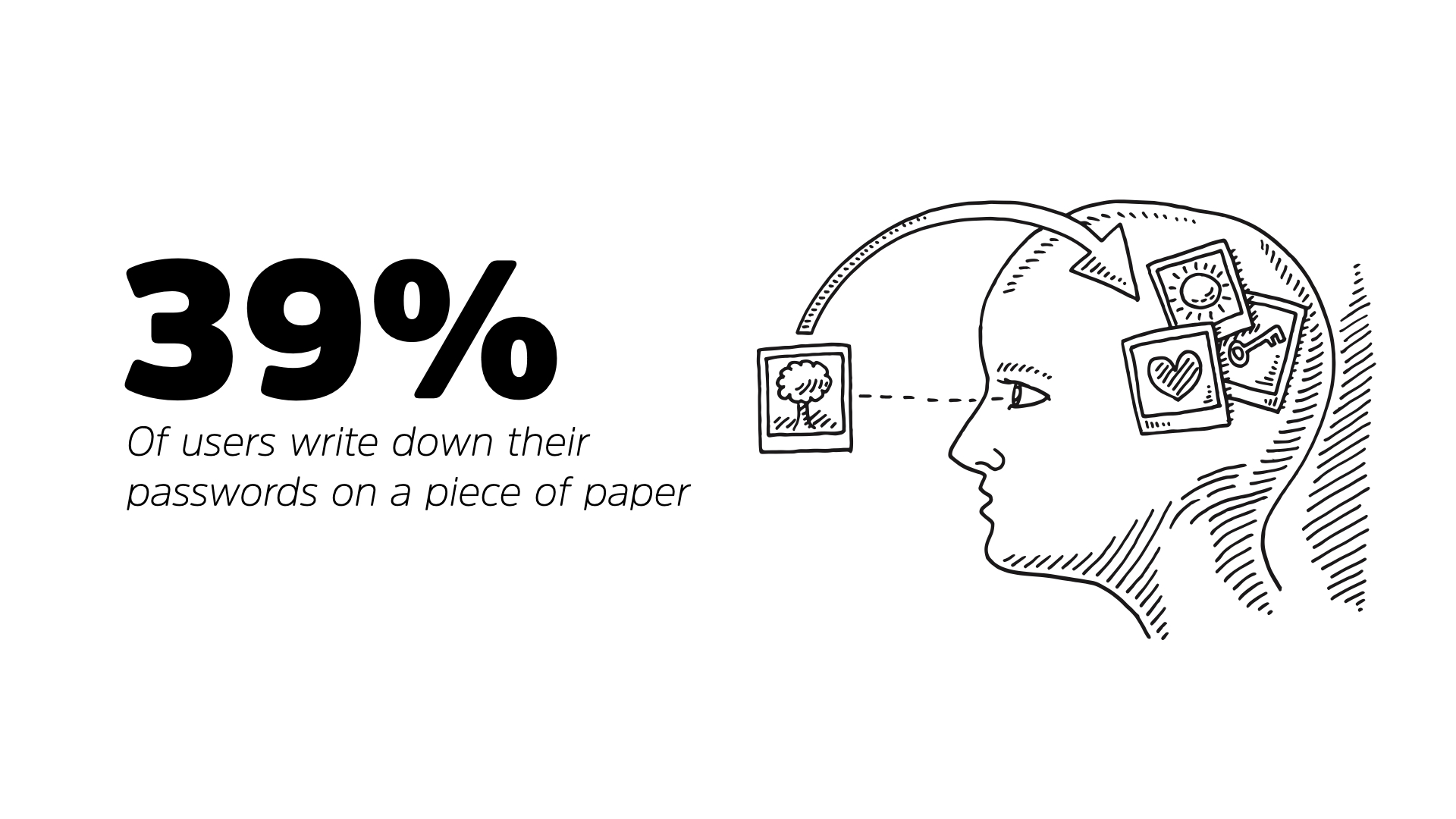
Now, most of this isn’t your fault. The security community has mishandled passwords since day one. 39% of users write down their passwords on a piece of paper and that’s not automatically a bad thing. That reduces the attack potential to a physical one which is better than the entire internet.
A better approach would be to use a password manager. It’s a tool that helps generate unique passwords for each app or service and you only have to remember one, strong password to unlock the manager

23:00
11pm and it’s finally time to call it a day. Yes, 11pm. Haven’t we seen enough today?

Zzz...

Wait a second, before we crash, let’s review the day.
1. Despite the headlines of hacks and breaches, we know that digital trackers are the real threat when we read news online

2. Nation state attacks are rare and rarely our concern. While we’re paying attention to those attacks, cybercriminals had an economic impact of 6T USD in 2018
3. Hollywood shows us hackers breaking through multiple firewalls in seconds but the real challenge is email. Most malware is dropped through tricking users to take an action that downloads the malware onto their own systems!
4. We constantly worry about losing our credit card info online because it’s a pain to update all of those automatic charge accounts, but the real issue is identity fraud. Scams of all sorts start with one piece of information about you and snowball from there
5. You rarely pay for credit card charges that aren’t yours but imposter fraud costs Americans 488M in 2018. It can take years for victims to recover
6. Wifi feels like a threat but a more direct issue is the “helpful” way your devices try to speed up connections by broadcasting past networks they’ve connected to. They are unintentionally mapping out your day
7. The idea of self-driving car scares a lot of people but the issue is the transitional phase and then human interaction in the future. Who will make these unthinkable decisions and add them to the driving model in the cars?
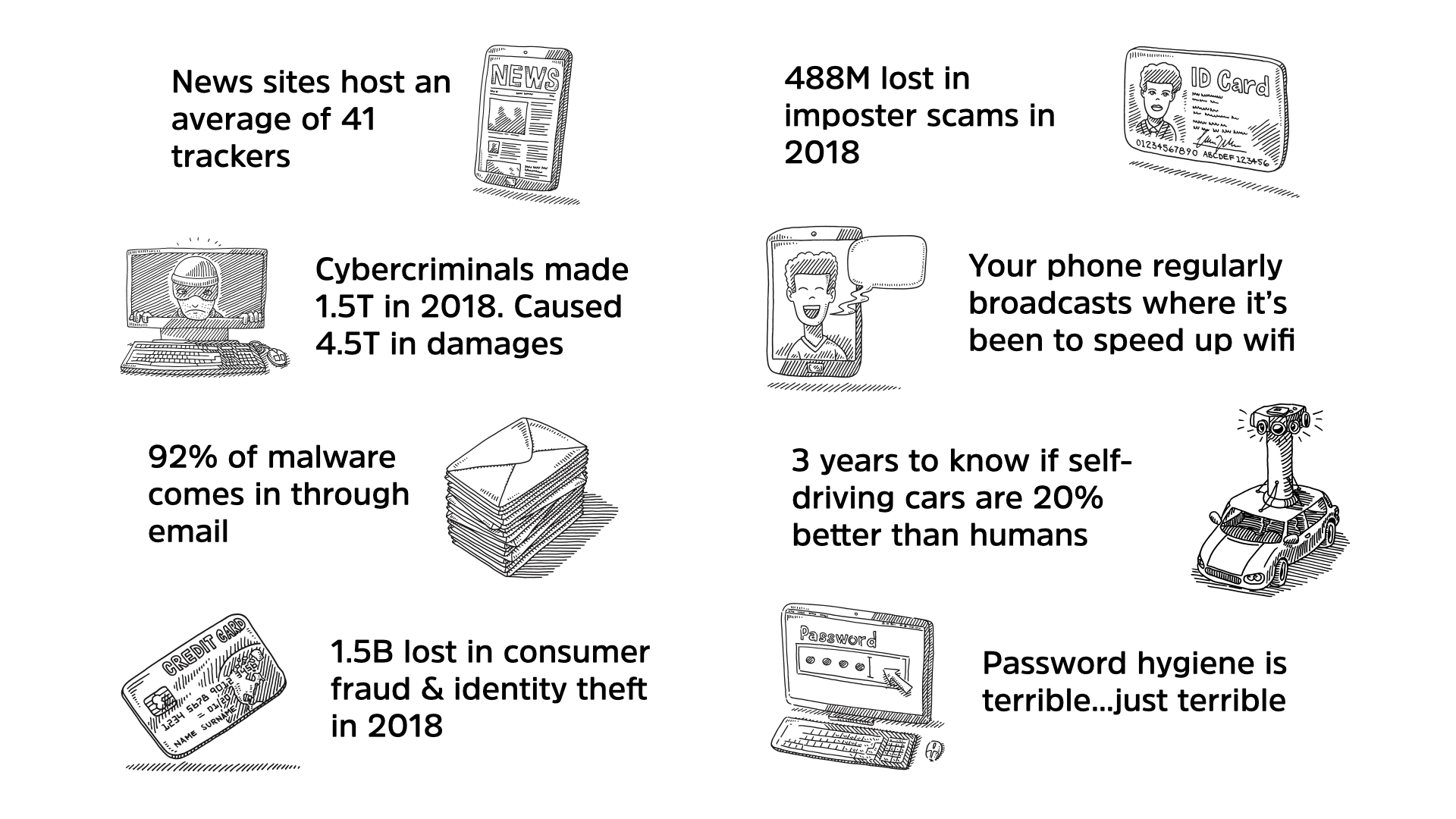
8. Passwords are terrible. But they are the best terrible of a host of other terrible options. Using a password manager can shift terrible to bearable and reduce the “blast radius” of a breach in your life

Some practical advice:
- Use privacy features/extensions in your browser to prevent tracking
- Auto-update all of your software & devices
- Monitor all of your accounts for fraud
- Don’t take action after clicking unknown links
- Use a password manager

Thank you! Please reach out and continue the discussion under the hashtag #fcfestival or hit me up directly @marknca