AWS re-launches a dramatically improved Amazon Inspector, a software vulnerability discovery/management service.
The idea behind these types of services is to scan your servers and containers before they reach production to identify known vulnerabilities so that you are aware of them and can mitigate them appropriately.
Notice I said “mitigate” not “patch”. Patching is just one of many possible mitigations.
Amazon Inspector launched in 2015 and a lot has changed since then. This is a much needed upgrade to the service that should help builders identify these issues with the minimal amount of effort possible.
This 👇 Twitter thread highlights some of the details of the launch…
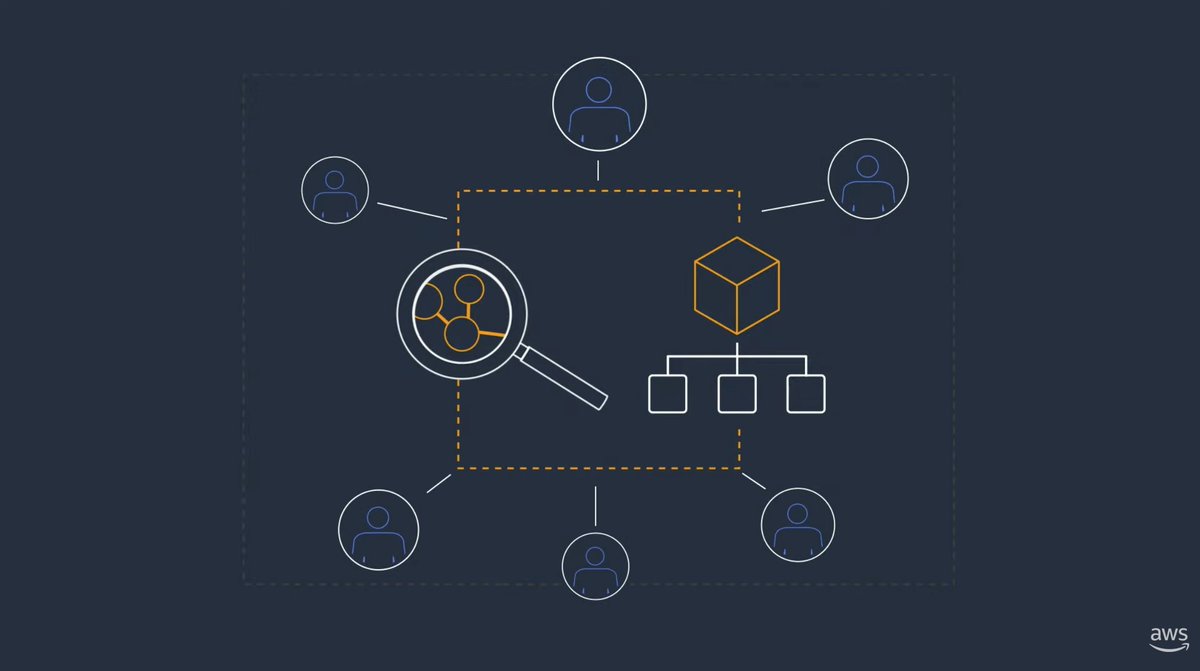
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 2/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 3/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 4/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 5/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 6/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 7/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 8/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 9/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 10/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52
Tweet 11/11 👇 Next tweet 👆 Start
@marknca tweeted at 29-Nov-2021, 20:52




