A purely digital RSAC is a fundamentally different experience. Gone are the happy run-ins between sessions, the energy is decidedly different, and it can be challenging to really grasp “the show.”
The good news? It’s a lot easier to focus on the content and not the flash of the expo halls.
I was fortunate to be able to attend this virtual conference and spent most of my time looking at the big themes of the keynotes and the sessions specifically focused on cloud security issues.
You need a pass for RSA to watch the full talks and access the slides but here’s a summary of what I experienced with a particular focus on ☁️ cloud and cloud security, along with my key takeaways…
Index
- Opening Keynote
- Other Keynote & Their Themes
- Project 2030: The Future of Cybercrime
- Blind Spots: Two Cloud Threats You Didn’t Even Know You Had
- Attack & Defend: Protecting Modern Distributed Applications and Components
- Cloud Threat Modeling - from Architecture Design to Application Development
- Multi-Cloud Anomaly Detection: Finding Threats Among Us in the Big 3 Clouds
- MITRE ATT&CK® as a Framework for Cloud Threat Investigation
- Attacking Kubernetes Clusters Through Your Network Plumbing
- Resources for Chaos Engineering
- Other cloud talks
Opening Keynote
The opening keynote featured a number of speakers and the classic “Cryptographers Panel.” A virtual keynote is always hard to pull off but the show did a reasonably good job.
The keynote was divided into easy to digest segments that flowed reasonably well around the theme of “resilience” (which is the theme for the entire show).
First up was Rohit Ghai, the CEO of RSA Security. Rohit’s short segment used three examples of resiliency and adaption in stressful times. What stood out for me was the call out for Netflix’s Chaos Monkey tool.
A cloud operations tools getting a call out in the first couple of minutes of a major security keynote is huge. It’s about time that modern tooling was front and center in the security community.
But the cloud side of me was disappointed. Chaos Monkey has been out in the open for 5 years! It should not take this long to get the modernization ball rolling for security teams. 😔
More on chaos engineering below…
After Rohit, Chuck Robbins, the CEO of Cisco highlighted the need for security everywhere and the required push for more diversity and inclusion in our community. As a major sponsor, it’s always hard to walk the line between company messaging and actual content and Chuck did well.
Next up was a great conversation between Angela Weinman, Head of Global Governance, Risk, and Compliance at VMWare, and Jimmy Sanders, Information Security at Netflix DVD. They spoke about the need for change in our community and provided three hard truths that we need to accept and move past.

Their take away was that we have to zoom out to gain perspective. Throw out old ways of doing things and regularly challenge our actions and perceptions. And finally to reach out and include more people and diverse viewpoints in our work.
Next up, poet Rives with a commentary on the past year and it’s impact on the security community.
After that, we had the annual math award and the storied “Cryptographers Panel.” The well deserved award went to David Pointcheval for his body of work around cryptography.
For more, watch my analysis with John from the Cube at the top of the page 👆 or you can read my Tweet-storm play-by-play here 👇.
opening keynote for #RSAC2021 kicking off now…#security— Mark Nunnikhoven (@marknca) May 17, 2021
Other Keynote & Their Themes
The other keynotes throughout the week looked a new attack techniques, current challenges with traditional security approaches, and issues around AI.
RSA offers sponsored spots within the keynotes so the educational quality of the information vs. the promise of the abstract varied. Some were excellent, others not so much.
Realistically, keynotes are targeted at a very broad audience and rarely go into enough depth to be of interest for well known-to-you issue. This year was no exception.
Though Anne Neuberger’s (Deputy Assistant to the President and Deputy National Security Advisor for Cyber and Emerging Technology, National Security Council) segment on, “Cybersecurity as a National Imperative” was an interesting lens into how the current US administration views cybersecurity.
Similarly Bruce Schneier’s (Security Technologist, Researcher, and Lecturer, Harvard Kennedy School) segment, “The Coming AI Hackers” was both entertaining and raised important issues in AI through a security lens.
Lots of work to do in this area.
Project 2030: The Future of Cybercrime
This session (SAT-M12) featured my good friend Rik Ferguson with Dr. Vic Baines discussing their newly released white paper, “Project 2030.”
This paper follows Project 2020 which was scarily accurate in it’s predictions. There’s no super cool video series (yet?) but the paper is well worth reading to get a feel for where cybercrime is heading in the next decade.
This isn’t a cloud-specific talk but I think the work is important enough to call out in this post. I’m really looking forward to see what Rik and Vic build from this initial whitepaper.
Blind Spots: Two Cloud Threats You Didn’t Even Know You Had
Matt Chiodi, Chief Security Officer for Public Cloud at Palo Alto gave a great talk discussing his teams finding around cloud threats. The talk, “Blind Spots: Two Cloud Threats You Didn’t Even Know You Had”
His main premise is one that I see over and over again, the biggest threat to cloud security is misconstructions.
Matt backed this up with a large dataset gather from customers and publicly available sources. I would’ve liked to see the split of public vs. customer as that would’ve provided an interesting data point showing any differences in actions taken internally vs. externally.
Still, the point remains the same, the potential complexity of cloud solutions presents a very real security challenge.
More in my tweet thread here 👇
busy day but managed to catch some more #RSAC2021 content
kudos to @mattchiodi from @PaloAltoNtwks for delivering a great _sponsored session_
why is it great?
1. Matt’s a great speaker
2. Lot’s of data in the talk
3. ZERO sales/company positioning (so far)
☁️ #cloud pic.twitter.com/wd9QJtqqbD— Mark Nunnikhoven (@marknca) May 17, 2021
Attack & Defend: Protecting Modern Distributed Applications and Components
This session (CSV-M07) from SANS instructors Johannes Ullrich & Jason Lam looks at a modern application from an API perspective.
Using a very simple example they highlight a number of different potential attack avenues. What impressed me with this talk was that these attack vectors line up with very common misconfigurations of cloud services.
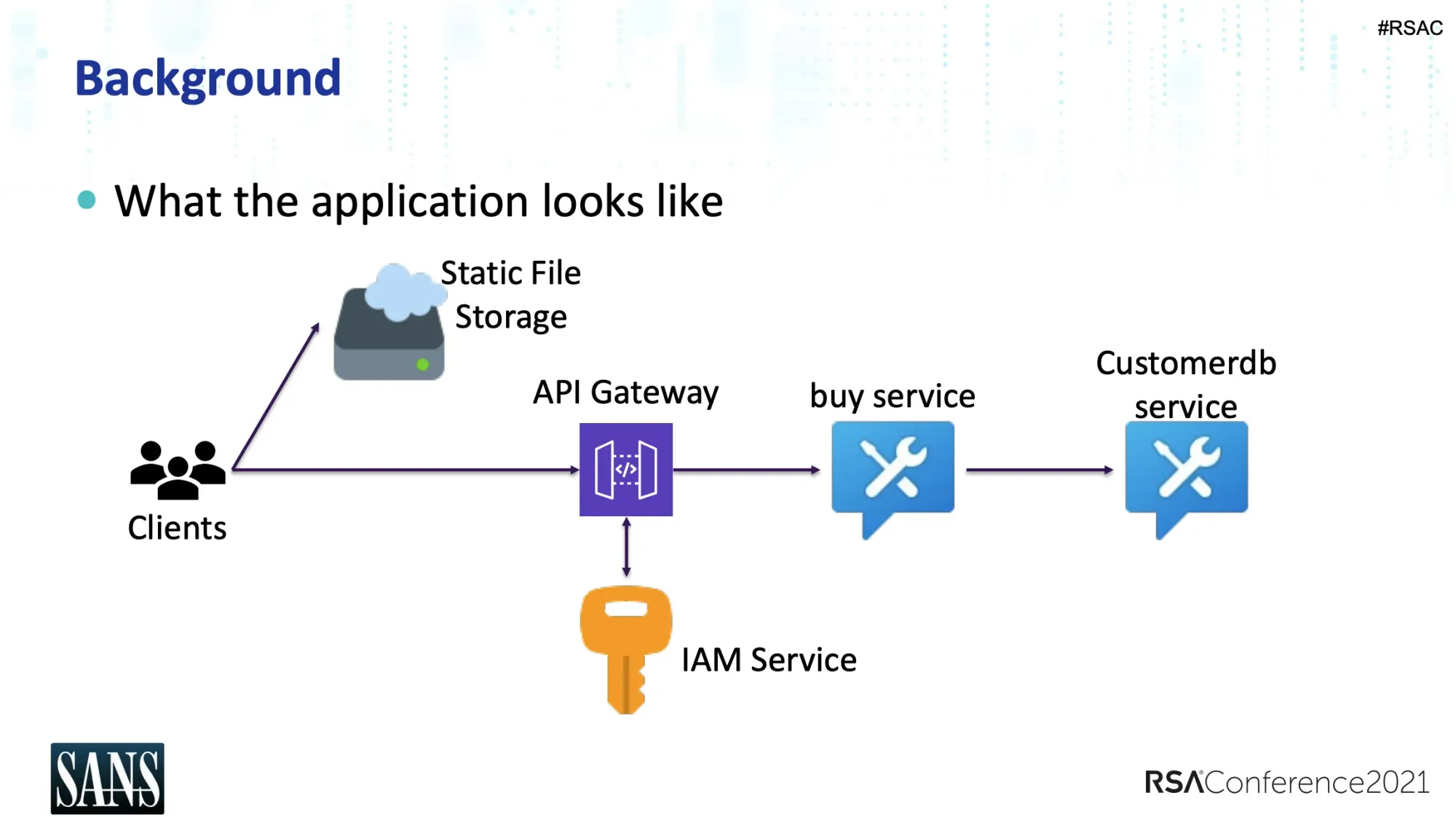
Johannes and Jason do a great job of walking through these scenarios in an easy to understand way. Great talk.
Cloud Threat Modeling - from Architecture Design to Application Development
This session (CSV-M08) features Randall Brooks, Principal Engineering Fellow, Raytheon Technology and Jon-Michael Brook, Principal Security Architect, Starbucks.
They start by introduced the basics of threat modeling conceptually and the compare some of the different approaches. Foundations in place, they move on to highlight some of the work that the Cloud Security Alliance’s (CSA) Top Threats working group has been doing.

Jon-Michael then walks through the CSA methodology for threat modeling. It useful to see the methodology applied vs. just reading the structure. The examples used in the session help drive that home.
Multi-Cloud Anomaly Detection: Finding Threats Among Us in the Big 3 Clouds
This excellent session (CSV-M15) features Brandon Evans from Zoom. Brandon is also an SANS instructor, regularly delivering SEC510, Public Cloud Security: AWS, Azure, and GCP.
Brandon does a great job of breaking down how each of the “big three” CSPs (AWS, Azure, and Google Cloud) handle logging network activity.
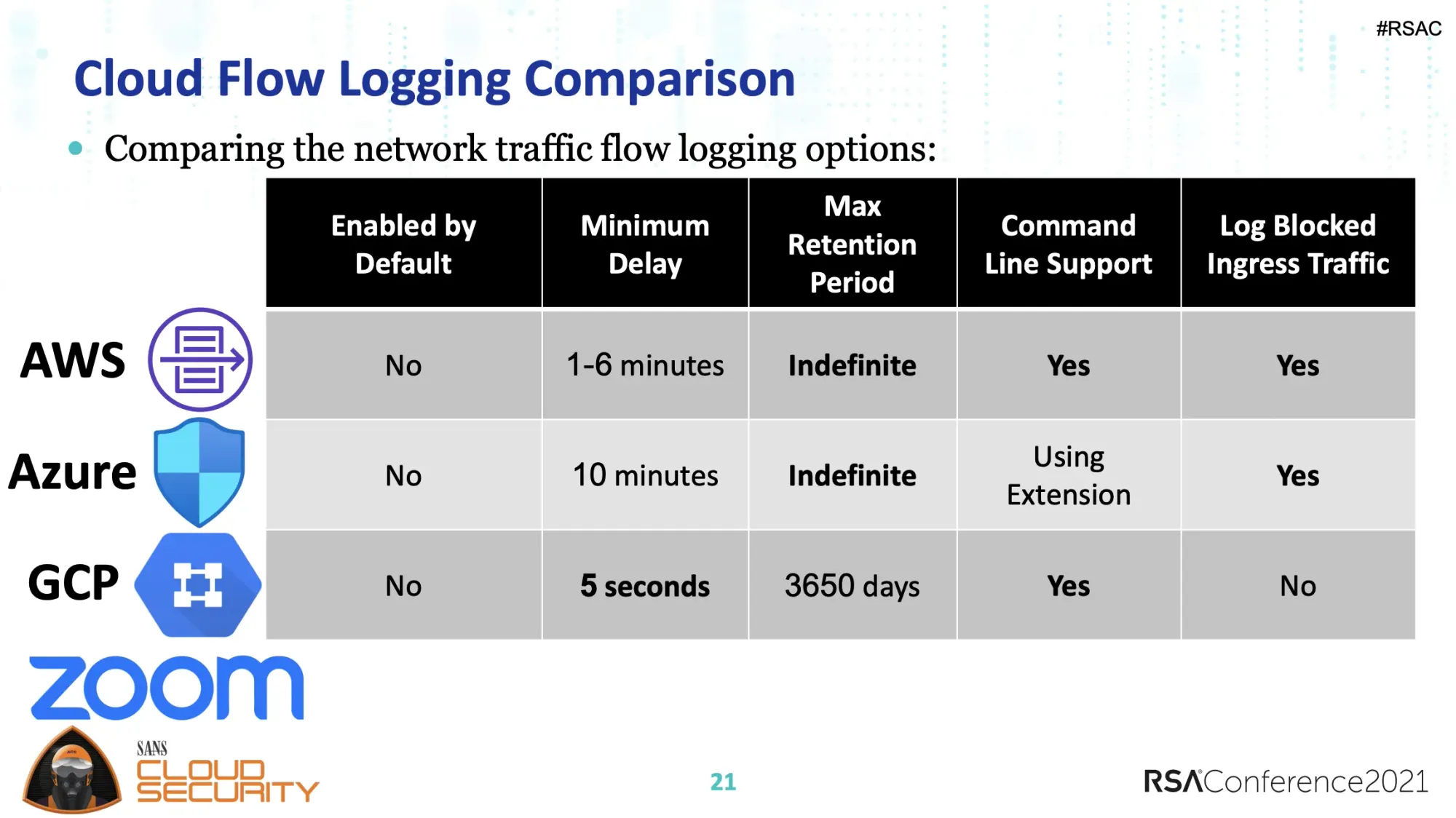
Later in the session, he also dives into API audit logging and how to create events and notifications based on those logs.
It’s absolutely possible to build out a log analysis and notification system using the CSPs own tooling. Brandon’s talk shows some of the edge cases and interesting quirk’s of each providers approach raising the key question; should you do this on your own or use a third party tool?
MITRE ATT&CK® as a Framework for Cloud Threat Investigation
This talk (CSV-W07) from graduate students Jasdeep Basra and Tanu Kaushik from CLTC Berkley looks at the possibility of using the
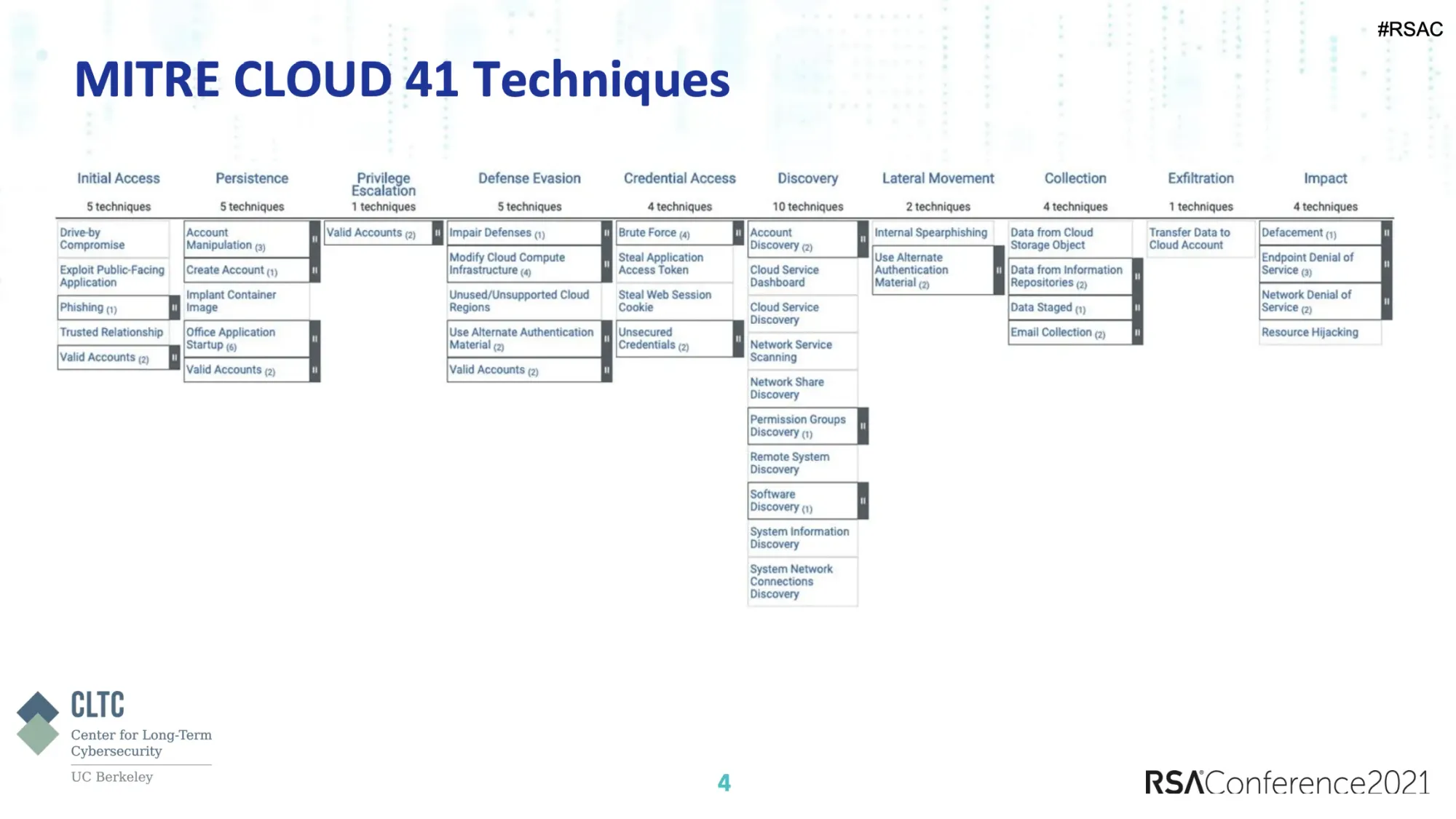
MITRE ATT&CK® framework to investigation cloud threats. Based on a survey they conducted (which popped up some odd CSP usage results), they explore using the framework investigate as opposed to using it to identifying gaps in security postures.
The talk pulls together some good ideas and shows us an area that definitely needs more attention.
Attacking Kubernetes Clusters Through Your Network Plumbing
This session (CSV-W09) from Nir Chako at CyberArk looks at how attackers target Kubernetes (k8s) clusters through various network layers.
After explaining the basics of networking in a k8S environment, Nir dives into layer specific issues.
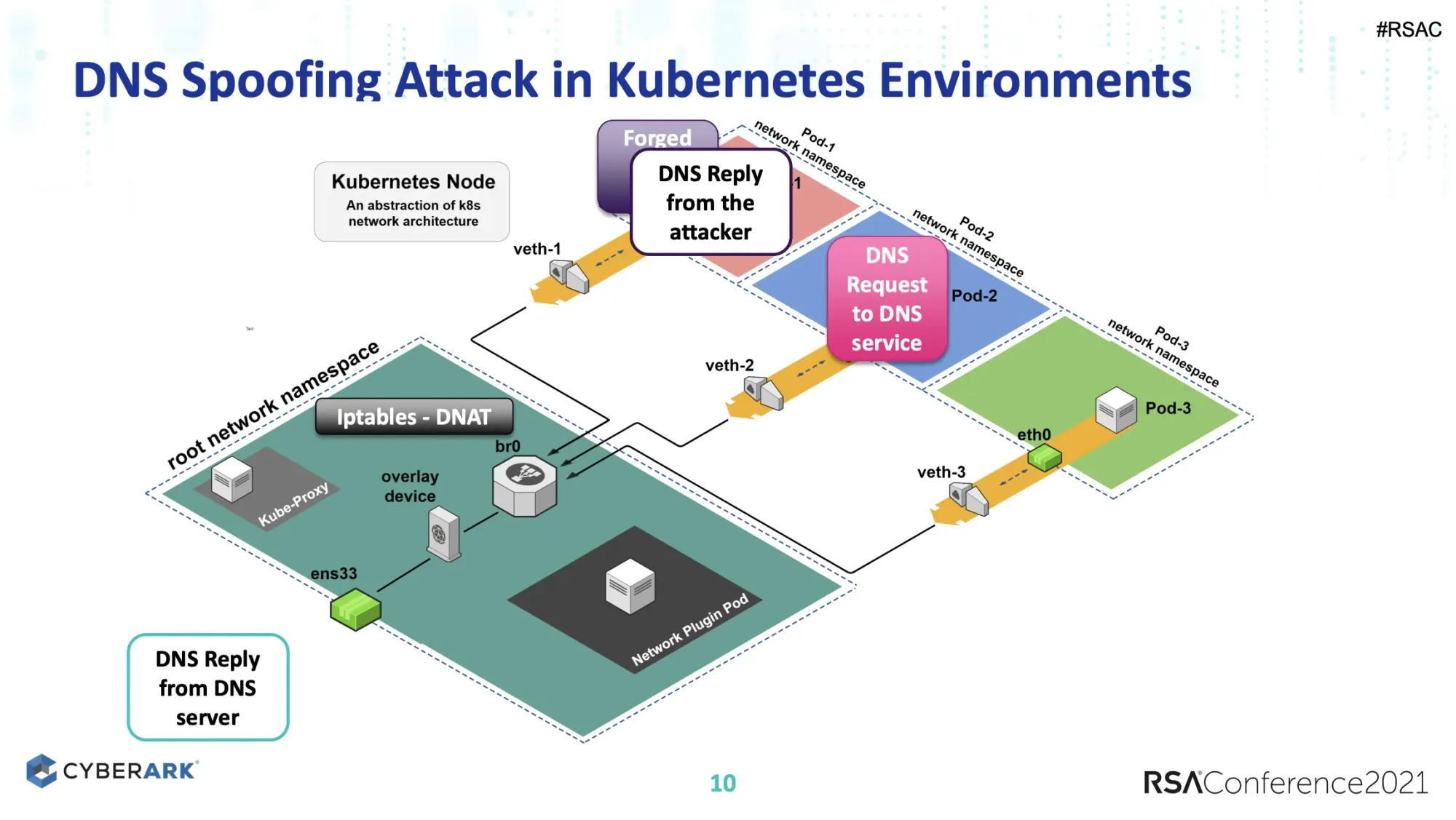
Showing a DNS spoofing attack via layer 2 and other attack scenarios. Similarly, Nir looks at layer 3 with routing and BGP issues.
I liked this talk because it looks at how real world attacks can be adapted to a widely distributed cloud infrastructure piece, Kubernetes. This is the type of practical information that security and infrastructure teams can use to improve their security posture.
Well done.
Chaos Engineering
Chaos engineering was mentioned in the keynote (yay!) and is an area that’s just coming into common use with cloud builders. Certainly AWS’s new AWS Fault Injection Simulator service is helping with that but a lot of work has been done in the community to make this approach more…um…approachable.
At it’s core, the idea is simple. You should be predicting how systems react during failure events and practice recovery. But you’ll never really know until it happens in an unpredictable way, thus tools like Chaos Monkey.
The easy analogy here is a fire drill. If you tell everyone that there’s a drill at 10:00 am, people will adjust their behaviours and the results of the drill won’t reflect reality. If you conduct the drill randomly with no heads up, you’ll a more accurate picture of how people would react in a real emergency.
Want to learn more? This InfoQ piece is a quick read to give you an idea but you really should dig into work of two experts in this area, Nora Jones and Kelly Shortridge.
This interview is a great place to start for Nora. This 2019 talk from Kelly is another great starting point.
Other Cloud Talks
These talks also focused on cloud but were either introductory, too “sponsor-y”, or didn’t introduce any new concepts.
That in of itself is telling and adds to my overall concern about the state of cloud security knowledge and the pace of security modernization but more on that below in the wrap up.
- Work Smarter Not Harder: Tips to Approach Cloud Security the Easier Way [SPO2-T15] by Erin Sindelar at Trend Micro
- Multi-Cloud Security Monitoring and CIS Benchmarks Evaluation at Scale [CSV-M17] from WM Global Technology Services
- Beyond Public Buckets: Lessons Learned on Attack Detection in the Cloud [AIR-T14] from F-Secure
- A Case Study of the Capital One Data Breach [RMG-T15] from C6 Bank
- Confidential Computing Across Multiple Clouds and Platforms: Project Enarx [OST-T15] from Red Hat
- Security Policy Management in the Hybrid Cloud [SPO2-T19] from Tufin
- What’s Old is New: Hybrid Security for Microsoft Azure and On-Premises Tech [CSV-W13] from Mandiant/FireEye
- Managing Access Entitlements & Their Lifecycle in a Multi-Cloud Environment [IDY-R05] from Microsoft
- Patterns for Encryption in Hybrid Cloud [STR-R06] from IBM
- Serverless Architecture Security Patterns for Securing the Unseen [DSO-R06] from Asurion
- Weak Links in Cloud IAM - Never Trust. Always Verify! [IDY-R09] from Palo Alto
- Due to Less Pollution, Secrets Stored on the Cloud are Now Clearly Visible [CSV-M14] from Splunk
Wrapping Up
RSA is a mainstay in the security community. For the past 30 years, the conference has brought together an amazing amount of security professionals to help further the craft.
The call for papers (CFP) is always frustratingly (from the point of view of a speaker) early but this serves an important purpose beyond conference logistics. The early CFP ensures that the conference isn’t full of talks about what’s happened in the last month. This approach allows the talks to focus on the bigger picture.
I take RSA as a good lens into the mainstream of the security community. What topics are of interest? What are practitioners currently tackling? What is keeping CISOs up at night?
With that in mind, this year’s RSA worried me.
There wasn’t nearly enough content focus on security modernization and cloud. What was in the agenda was mainly exploring how to take a traditional approach to a new problem (not a recipe for success) or introductory material.
Introductory material is always required, especially in a inclusive community. There will always be new practitioners starting out.
But 15 years into cloud, we really should be seeing more talks around automation, creating a data-driven security approach, and how to build better systems.
The theme of the conference was “resilience.” Based on the talks during the show, maybe we need to educate more security professionals on what modern resilience looks like. We have to move beyond simply stopping cybercriminals and attacks to helping organizations build better.
We have to help our organizations be better.