My last few posts have looked at the impact you can expect hybrid and full cloud environments to have on your security practice. I’ve called out incident response , monitoring , and forensics as areas that can benefit from the flexibility provided by cloud environments.
But what about the big picture? How do these areas come together to form your overall security practice?
The Big Picture, Literally
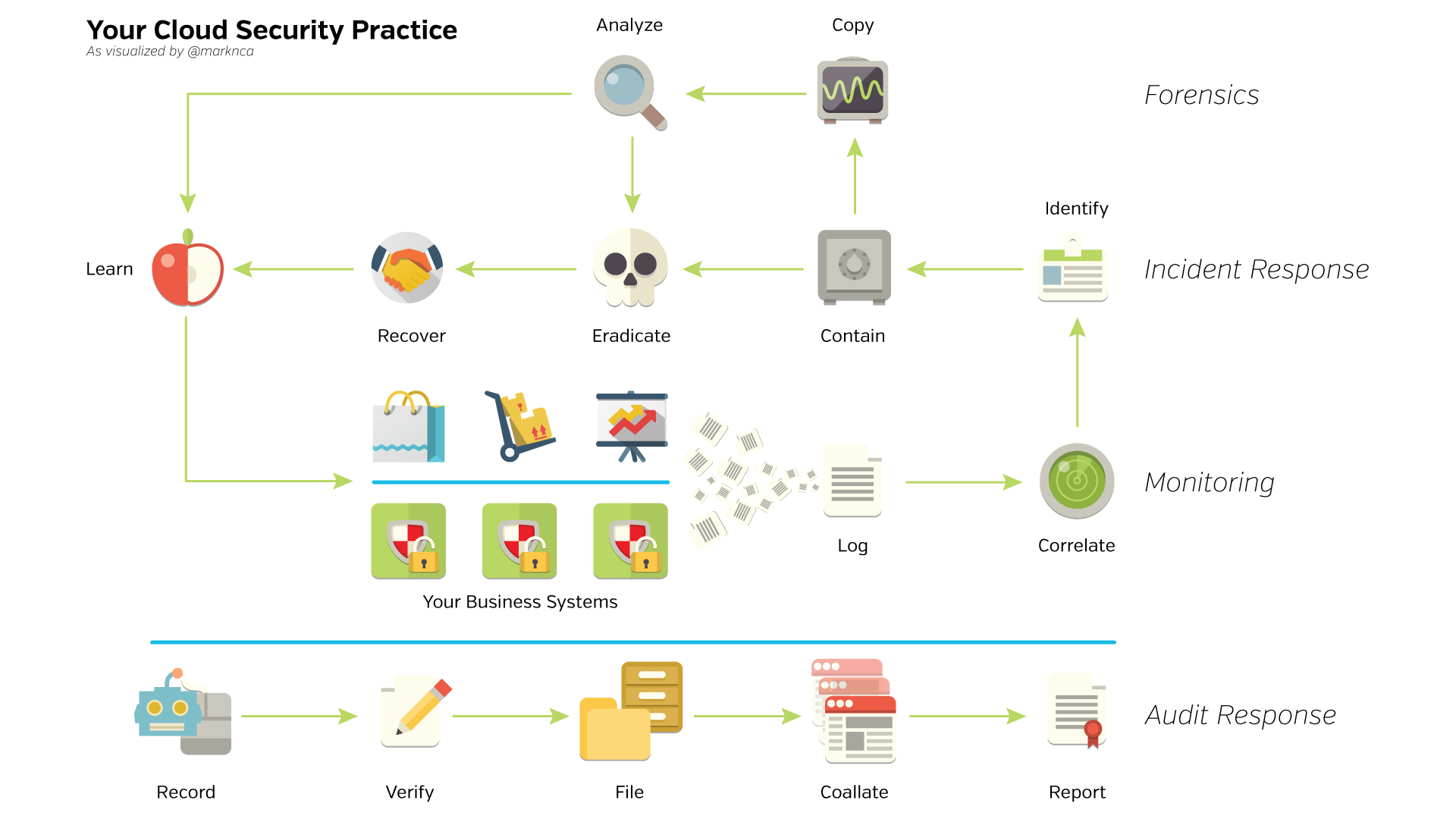
This image is licensed BY-NC-SA, please share it!
This image lays out how the distinct areas of your security practice flow together. Start in the middle with “Your Business Systems” and simply move along the arrow path. At the bottom, you’ll see the foundation audit response flow.
Everything in the practice adds to the audit response which is why it’s called out at the bottom.
Changes In The Cloud
The workflow laid out in the diagram isn’t really all that different from a traditional security practice. The important differences lie in the implementation.
Moving into the cloud provides the opportunity to enhance our practice with one underlying principle: automation.
Almost every one of these activities can be highly automated in the cloud. Automation comes with numerous benefits, but the major improvement is that it moves security operations firmly into the category of “business enablement.” If your business applications are deployed in a highly available, resilient manner, your security must be as well.
Automation will help you achieve that.
Take for example the deployment of the basic security controls themselves. If your application is designed to automatically scale based on user demand, your controls must automatically deploy and activate right alongside the application.
If they don’t, you’re either crippling your deployment by removing the elasticity the cloud provides, or your deployment is left without security until you can manually deploy.
From a tactical point of view, automating various practices like containment, recovery, analysis, audit response, and others, continues the theme of ensuring that security is flexible and can leverage the power inherit in the new cloud model for operations.
Amplifier
If you can push automation into all aspects of your security practice, not only will you be seen as an “enabler” for the business, but you’ll also be able to do more with the resources you have.
If you free up your analysts from work that can be automated, you allow them time to focus on the aspects that require a human, in-depth analysis (forensic and otherwise). Planning, awareness training, auditing, etc., are now not only possible, but will also continue to improve your practice.
Automation offers you the chance to finally stop reacting and to get out from behind the 8-ball. That’s something we’ve all pushed for over the years. If we embrace the possibilities and leverage the power of cloud deployments, it’s something we might actually get.