I’ve written about how monitoring and incident response change in hybrid and full cloud environments as part of this series on operations. This post is going to touch on the changes facing forensics in cloud environments.
Define Forensics
Before we dive in, I wanted to highlight that there are two definitions of “forensics” in use today. The most common of which means digging into an incident to determine what happened, step-by-step.
The technical definition (as per Google) is, “scientific tests or techniques used in connection with the detection of crime”. There are a few key words there, but at its core, it’s the same as our first definition with a whole lot more paperwork piled on.
Forensics in the law enforcement/legal sense is the same concept, but it comes with a significantly higher level of rigour around the techniques and documentation. Forensics as a discipline is not like you see it on TV crime dramas. You don’t (usually) get a lab coat, and it takes a lot longer than the 30 seconds of screen time it gets.
For this post, we’re going to address forensics in the common sense… looking into an incident to determine what happened.
Copy That
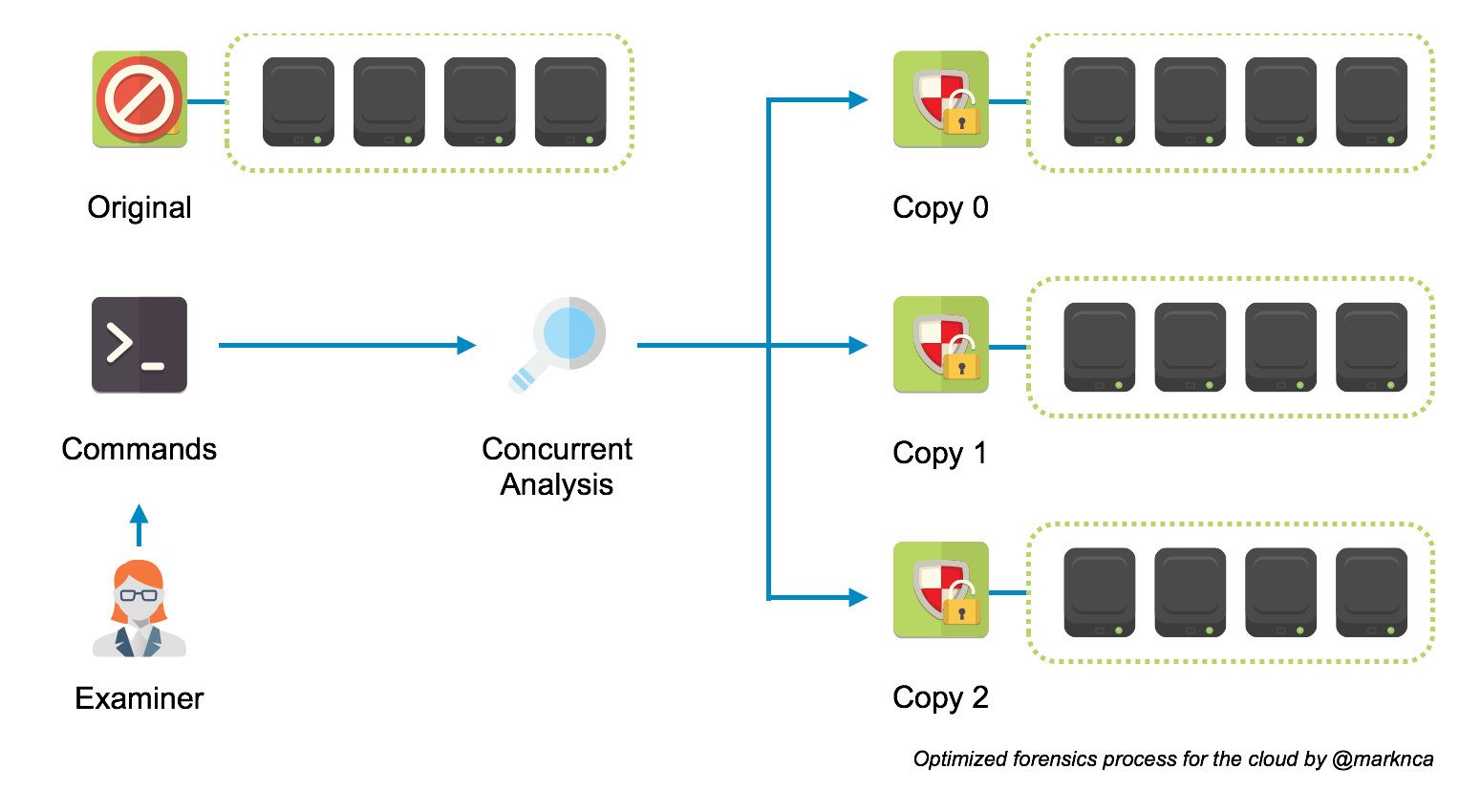
Step one in a solid forensics procedure is to make read-only copy of the system you’re investigating. In a traditional environment, you are typically constrained by available hardware, or, at the very least, storage space. In the cloud, that’s rarely an issue so we’re already ahead of the game.
Because we need to work on a read-only copy, we can use the abundance of resources available in the cloud to make forensics a highly parallelized process.
This is a huge boon to the investigation. Combing through a TB of data block-by-block can be time-consuming. If you’re searching for multiple keywords and artifacts you can simply run each of these searches in parallel on a duplicate of the original system.
This image is licensed BY-NC-SA; please share it!
The flexibility lets you optimize the human portion of the process. It’s a game changer that will greatly decrease the time to resolution for investigations.
Repeatability
Everything in the cloud is based around an API model. During an investigation, you can benefit from this by including the API calls and commands in your report.
Now, if your work needs to be repeated (very common in law enforcement and legal contexts), the only thing required is read-only access to the original data.
This continues the trend we’ve seen in monitoring and incident response where leveraging automation and the power of the cloud has immediate security pay-offs.
What’s Next?
Forensics is a major topic, and we’ve only seen a hint of the impact that hybrid and cloud environments will have on this area of your practice. Please add you thoughts in the comments below or on Twitter (where I’m @marknca).
As a reminder, next week (24-Mar-2014), I’ll be on the west coast at the AWS Summit in San Francisco and then on the east coast at AtlSecCon in Halifax talking about updating security operations to handle hybrid and cloud environments.
If you’re attending either of these great events, be sure to stop by and say hello.