Lately, I’ve been looking at our approach to updating security operations to deal with the realities of hybrid and full cloud environments. If you’ve missed the series so far, I’d recommend reading the first and second posts now.
This post is going to highlight a few of the challenges that your network security monitoring practice is going to face.
I tackled this topic in full-length sessions at AtlSecCon and SecTor last year. The reason I keep coming back to this topic is that it’s an area we handle reasonably well in data centre environments, but it’s undergoing a major change in cloud environments.
Monitoring is a key piece of any security practice, and if you don’t adjust for the realities of hybrid environments, you’re putting your practice at risk.
What is monitoring?
Richard Bejtlich gives a great definition in his book, The Tao Of Network Security Monitoring ; he states that network security monitoring is, “The collection, analysis, and escalation of indications and warnings to detect and respond to intrusions.”
This is a good place to start, but I find it’s a little too restrictive. The last part of the definition is too specific for my taste. The exclusive focus on intrusions—while in line with a security initiative—means that you’re not getting the maximum value out of your monitoring investment.
There’s a lot of cross-over between network security monitoring and performance monitoring. If you ignore that, you’re doing yourself a disservice. I’ll tell you from personal experience that it’s a lot easier to regularly tie performance monitoring to business outcomes, which means it’s easier to lobby for budget when the time comes.
For our purposes, let’s use my revised, slightly broader definition, “Monitoring is collection, analysis, and reaction to indications and warnings in your environment.”
That leads us to the creation of three phases:
- Collect
- Analyze
- React
Activities during each of these phases are affected by the move to hybrid and full cloud environments. For this post, we’re going to touch on the biggest change that is present in all three phases.
To understand that change, we’ll look at how we monitor data centre environments today.
Monitoring The Data Centre
In the data centre, we have the advantage (at least it’s an advantage in this case) of owning all of the points data must travel when transiting the network.
This includes all of the switches, security devices, and services that a request touches along the way. You can see this below.
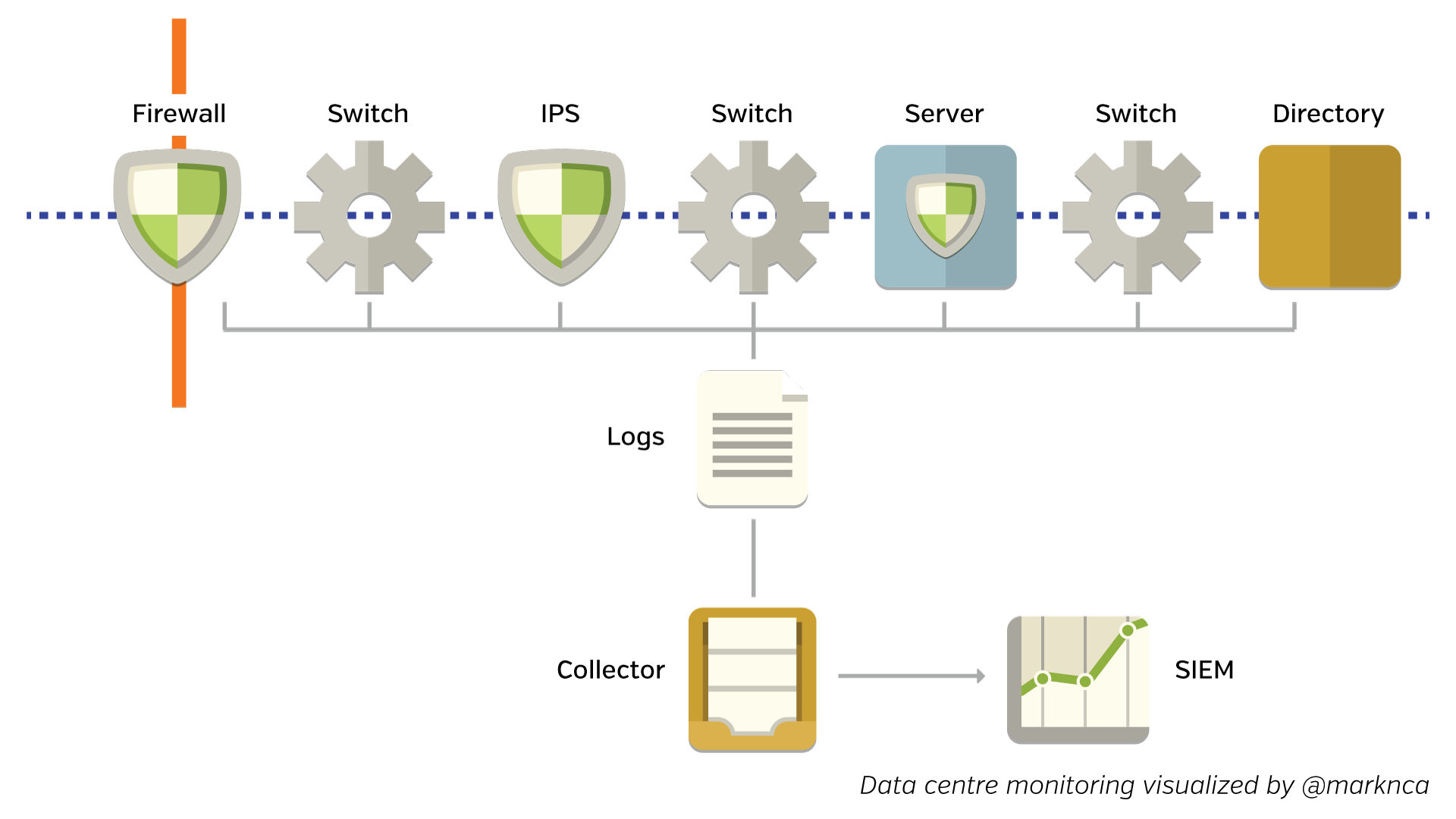
Please feel free to share this; it’s licensed BY-NC-SA.
Each of these devices sends a log file downstream. The logs are collected and sent to a Security Information and Event Manager (SIEM). The SIEM normalizes, scores, and correlates all of the information to try and create possible incidents for further analysis.
SIEMs have been designed with this network design in mind. Many small data points along the route of a data stream help the device piece together an accurate picture of what’s actually happening.
Monitoring Hybrid & Cloud Environments
When we move to the cloud, the story changes. The underlying principles are the same, but our data sampling changes. You can see the differences below.
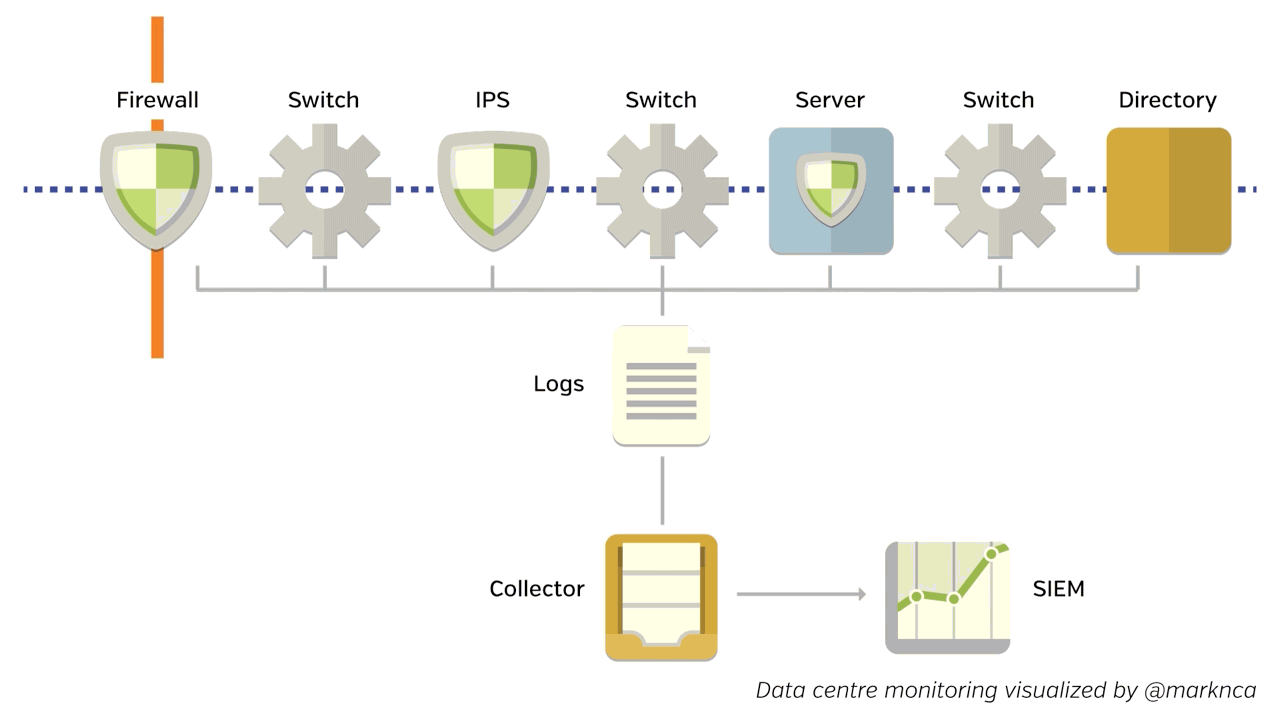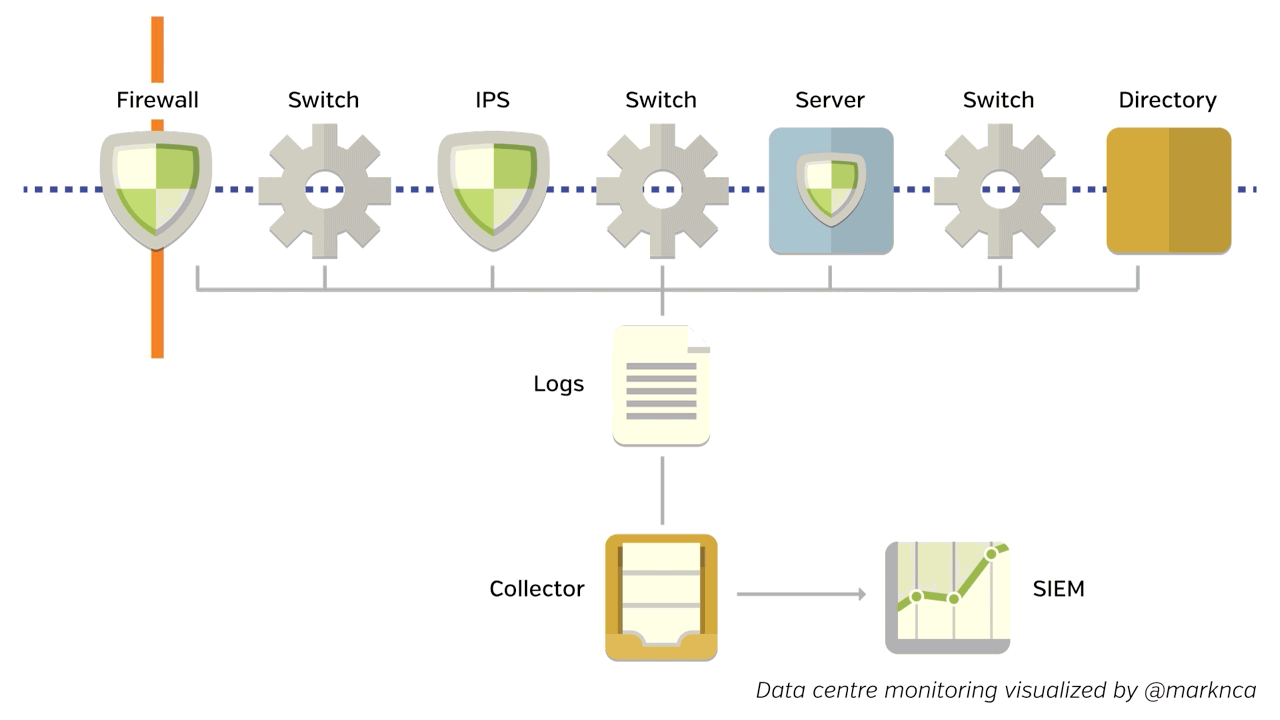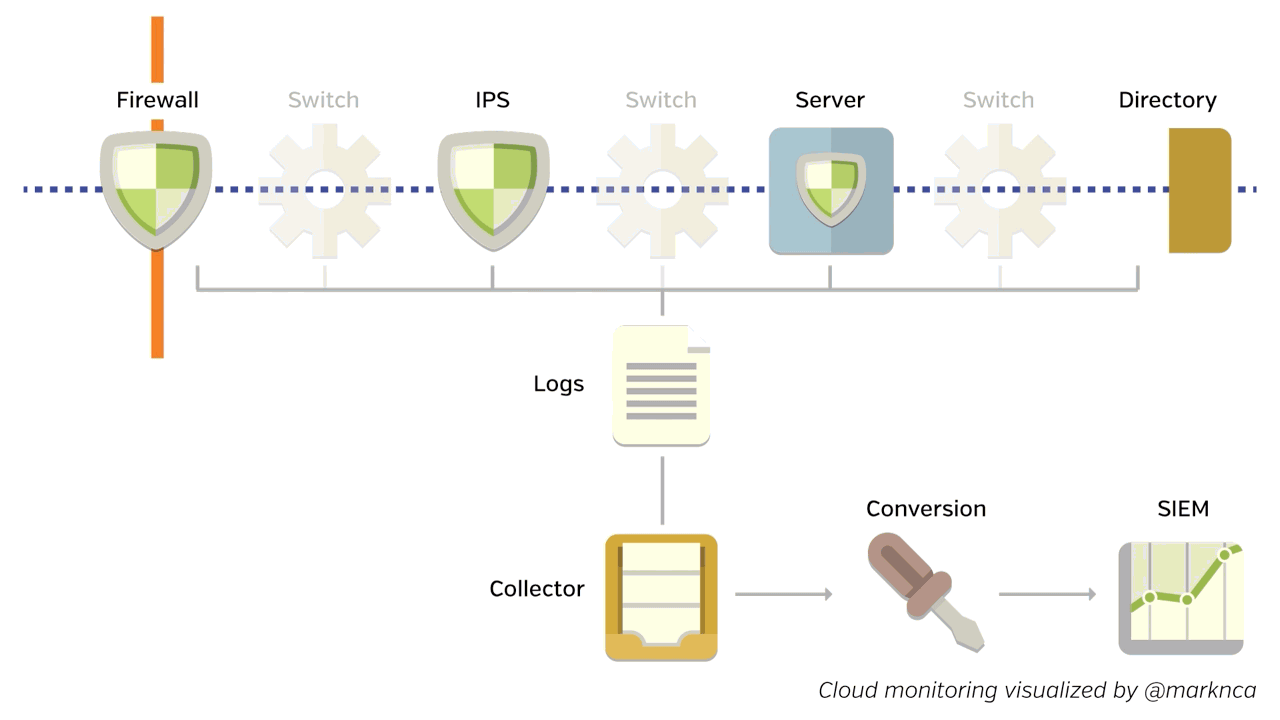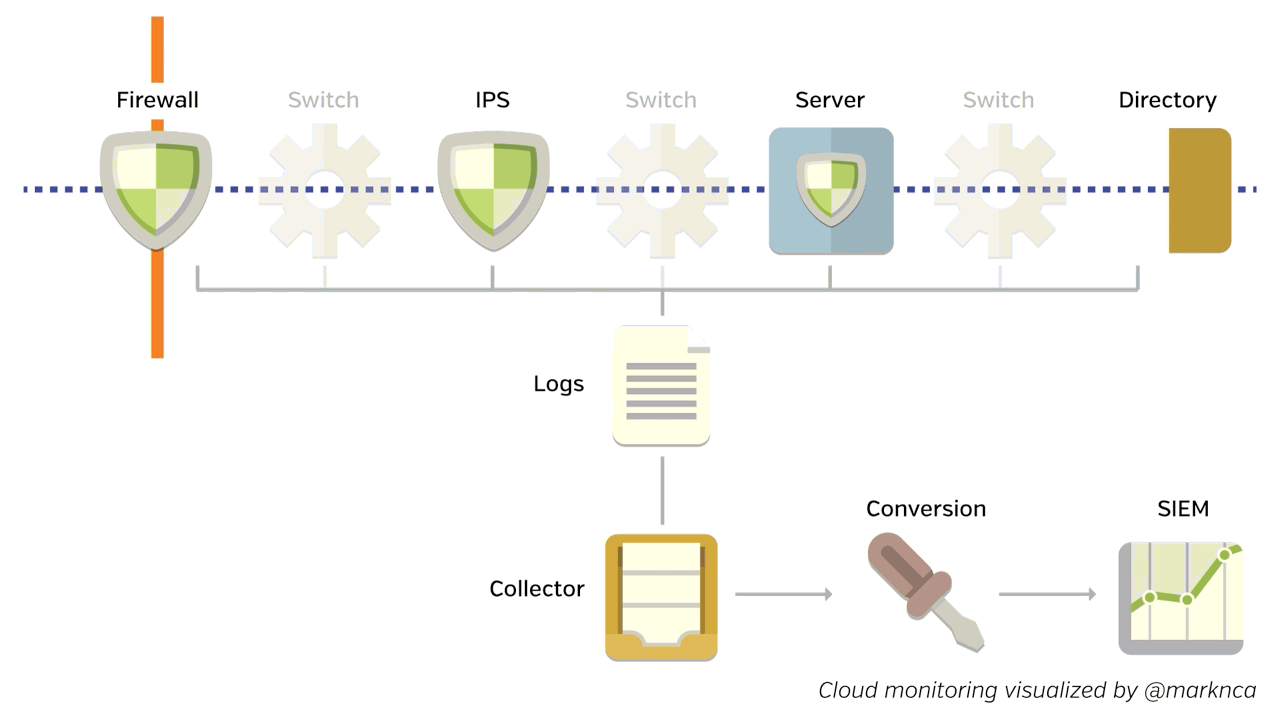
Please feel free to share this; it’s licensed BY-NC-SA.
We not only lose data points (which are now owned & operated by our cloud provider), but the data we do receive may be in different formats or through different channels.
This challenge isn’t insurmountable, but off-the-shelf solutions are just now starting to catch up. This is going to be an active area of development for the next few release cycles in the SIEM space.
But in operations, we don’t have the luxury of waiting for the next next release or even the one after that.
That means we’ll be deploying a home-brewed intermediary for the time being. That intermediary is going to be doing some custom conversion work for us. It’ll help our existing analysis tools (like a SIEM) understand the data we are receiving from our cloud service providers and our other cloud-focused tools.
What’s Next?
Despite the challenges that hybrid and full cloud environments present, there are also a lot of opportunities to improve our monitoring practices as we move to the cloud. Fortunately for us, the DevOps movement continues to have an intense focus on environmental monitoring. This is a great opportunity for security to integrate with existing efforts.
This post has only brushed the surface of the monitoring space. Please add you thoughts in the comments below or on Twitter (where I’m @marknca). This is a great chance to work together to help build hooks for security monitoring into existing cloud operations projects.
As a reminder, I’ll be on the west coast at the AWS Summit in San Francisco and then on the east coast at AtlSecCon in Halifax talking about updating security operations to handle hybrid and cloud environments.
If you’re attending either of these great events, be sure to stop by and say hello.